User rights audit
This section looks at how access is utilised by users. The topics covered in this section are:
Introduction
This report provides an indepth view of how assigned privileged access to device tools and tasks are utilised by users. Each time a user accesses a device task/tool, Osirium PAM audits the performed action and collates the data. The audited data is then pulled together to form a behaviour pattern. These behaviour patterns will allow you to quickly and easily see how access is being used by your users.
You can use the data presented in these reports to help tighten security on over privileged access as well as pinpoint access that is no longer required by a user, which can therefore be removed.
Each tab looks at different aspects of user behaviour and provides a graphical representation of the data.
Summary tab
This report provides an overview of the data analysed and shows in percentages how the user is using the system and what they are doing when logged in. If there are users that have never logged in then you should be asking why and whether access is still required by them.
The tasks and tools in profiles pie charts, represent the percentage of tools/tasks that are either being used or unused. Unused tools/tasks should be investigated and removed from profiles if no longer required to ensure a least privilege model.
As your organisations structure evolves, employees move job roles or departments, others may leave the company, it is therefore recommended that these reports are reviewed on a regular basis. They can help you identify changes in user behaviour so they can be updated according. This will ensure you apply a least privilege model, reduce over access and keep your environment secure.
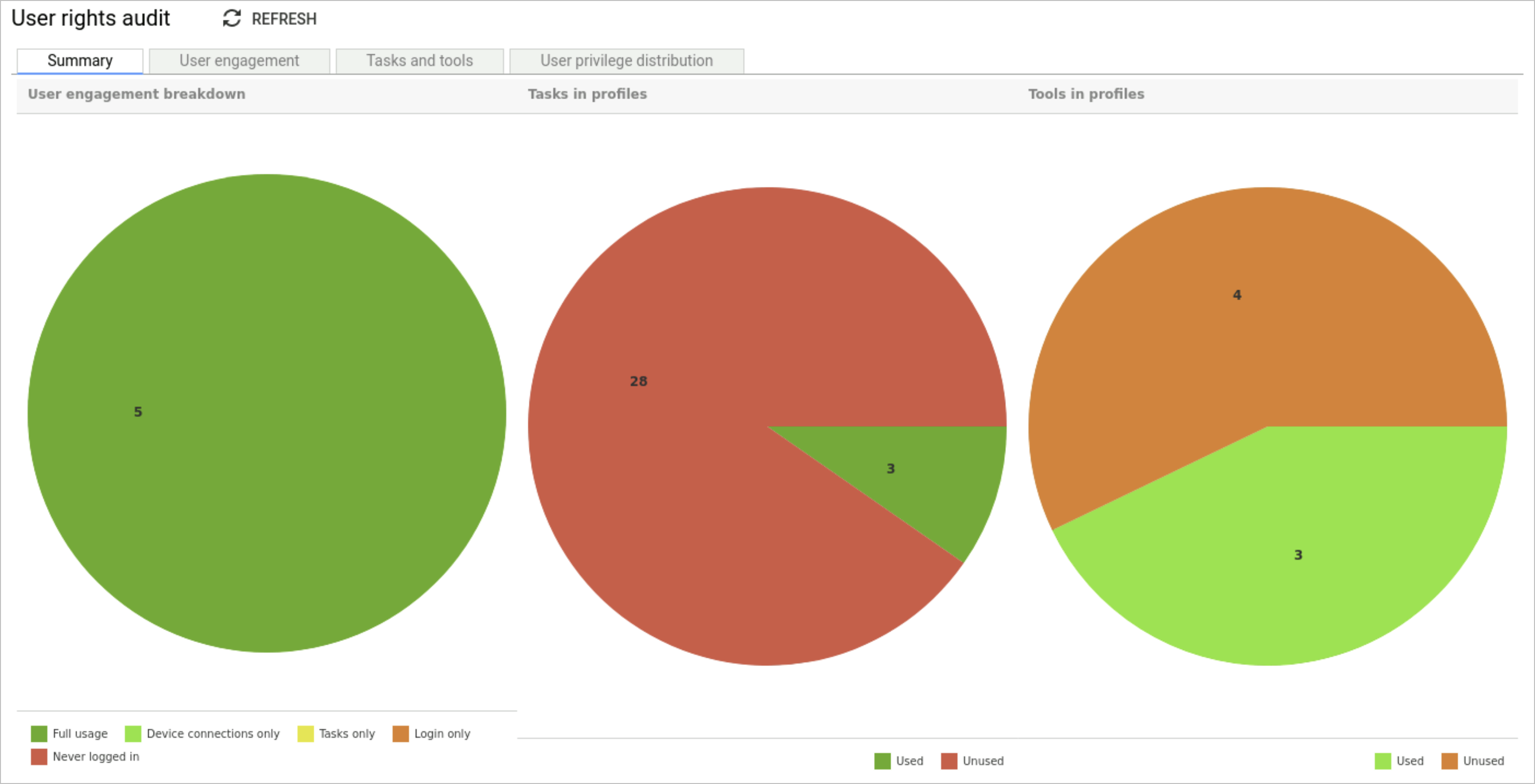
The following information is presented in the pie charts:
| Key | Description |
|---|---|
 Full usage Full usage |
The total number of users that have logged onto the UI, run tasks and made device connections. |
 Device connections only Device connections only |
The number of users that have made device connections only. |
 Tasks only Tasks only |
The number of users that have only run tasks. |
 Login only Login only |
The number of users that have logged onto the UI. |
 Never logged in Never logged in |
The number of users that have never logged onto the UI. |
 Used Used |
The number of users that have used tasks/tools. |
 Unused Unused |
The number of users that have not used tasks/tools. |
User engagement
This report gives you a breakdown of what each user is accessing and helps you analyse their activity.
From this report you can view the number of times a user has logged onto to Osirium PAM, connected to a device tool or ran a device task.
The information presented provides a useful insight from which you can determine low usage and to further investigate the reason why a user may not be using Osirium PAM to manage devices and run tasks.
From this analysis you can update access requirements to ensure over privilege is not granted. But also look at at high usage and ask yourself what is the user having to do regularly and can it be automated to save time.
The user activity data is presented within a table as well as a Gnatt chart.
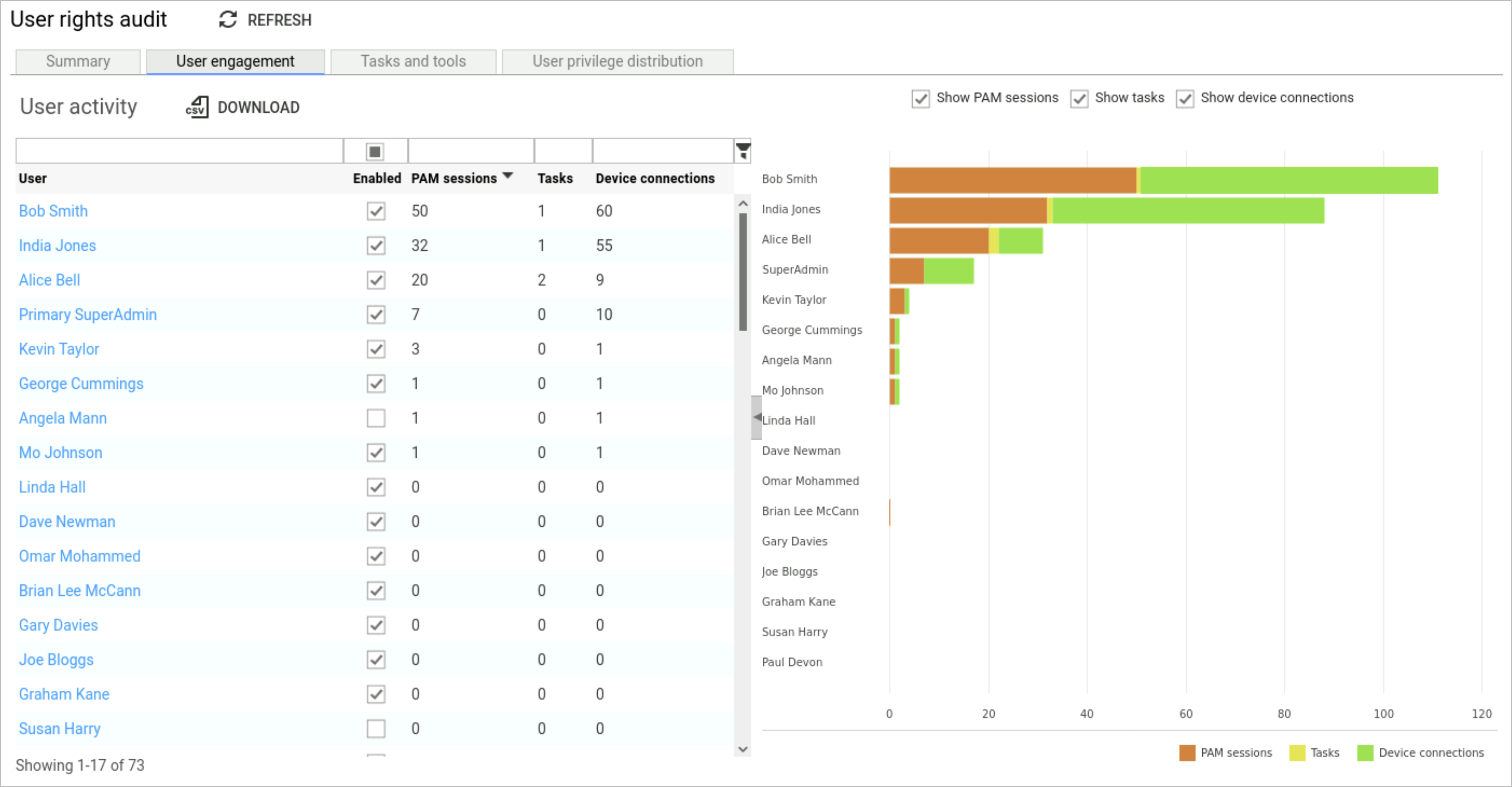
User activity
The information presented on this page is as follows:
| Heading | Description |
|---|---|
| User | Name of the UI user. |
| Enabled | Indicates if the user is able to connect to the UI (Enabled) or if the user account has been disabled. |
| PAM sessions | The number of times a user has logged onto the UI. |
| Tasks | The number of times a user has run a task. |
| Device connections | The number of times a user has connected to a tool. |
You can use this table to determine low user usage and investigate the reason why a user may not be using the UI to manage devices and run tasks.
Tasks and tools
This report breaks down the tasks and tools that are in a profile and if they have been used or unused.
From this data you can look at reducing overall user privileges to tighten up security, and also reduce access to tools and tasks. Use the data presented to help you investigate remove over privileges granted through various profiles.
You should be asking yourself if access configured in a profile has never been used then why hasn’t it and is it still required.
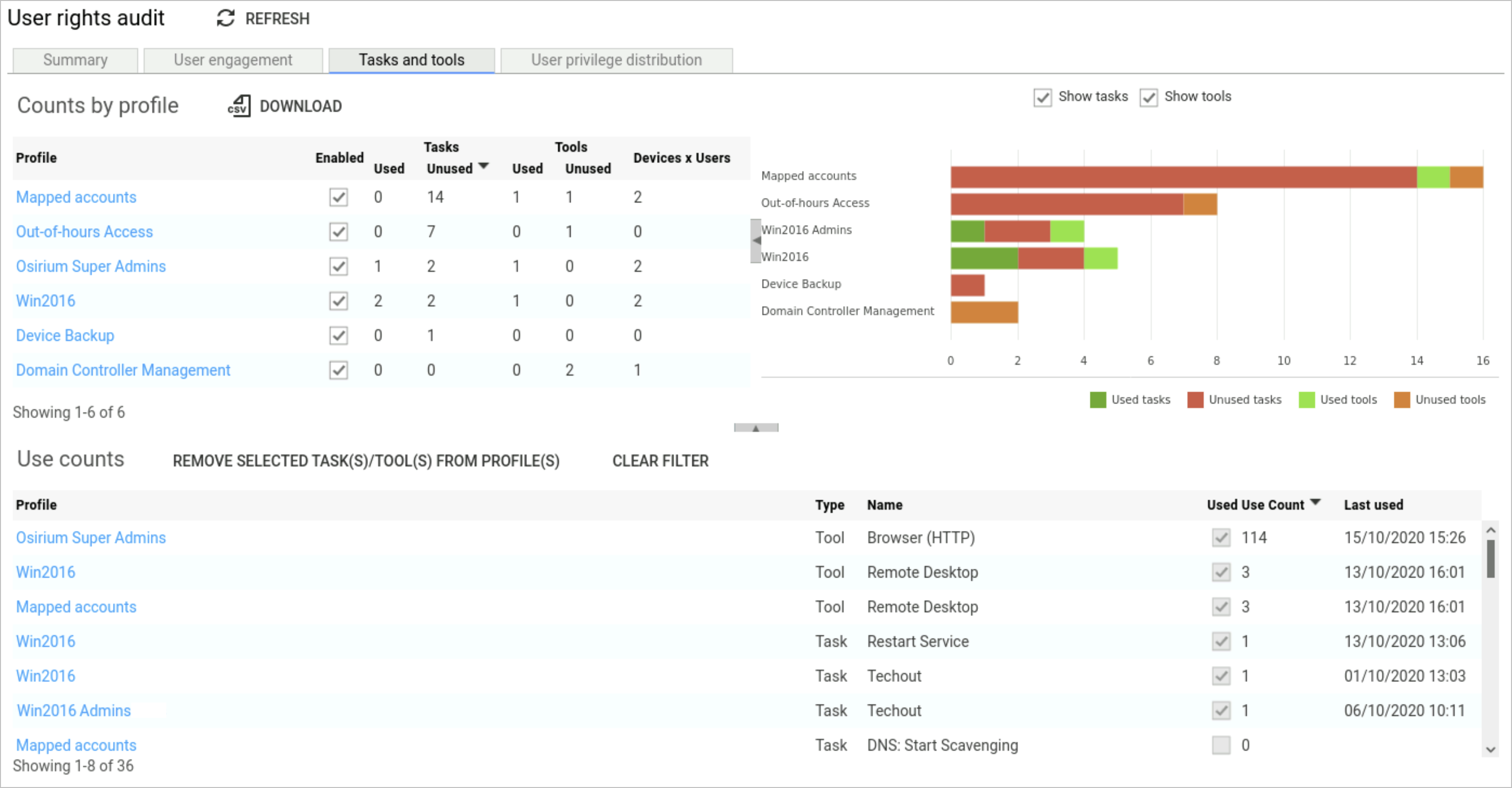
Counts by profile
The Counts by profile table mirrors the Gantt chart opposite.
The information presented on this page is as follows:
| Heading | Description |
|---|---|
| Profile | Name of the profile the tools and tasks are configured in. |
| Enabled | Indicates if the profile is Enabled to allow users access to tools and tasks through the UI. |
| Tasks | Shows the total number of tasks used/unused within the profile. |
| Tools | Shows the total number of tools used/unused within the profile. |
| Device x Users | Shows the total number of devices x users within the profile. Sort this column in descending order to view the severity. The higher numbers in this column should be reviewed against unused tools and tasks in a Profile, to improve and reduce user privileges. |
Use counts
The use counts data presented in the table can be used to quickly remove any access that has been investigate and deemed to be no longer required.
To quickly remove any access, simply select a row within the table and click REMOVE SELECTED TASK(S)/TOOLS(S) FROM THE PROFILE.
The information presented in the table is as follows:
| Heading | Description |
|---|---|
| Profile | Name of the profile the tools and tasks are configured in. |
| Type | Indicates if the access replates to a tool or task. |
| Name | Name of the tool or task. |
| Used | Indicates if the the tool/task has been used. |
| last used | The date/time the tool/task was last accessed by a user. |
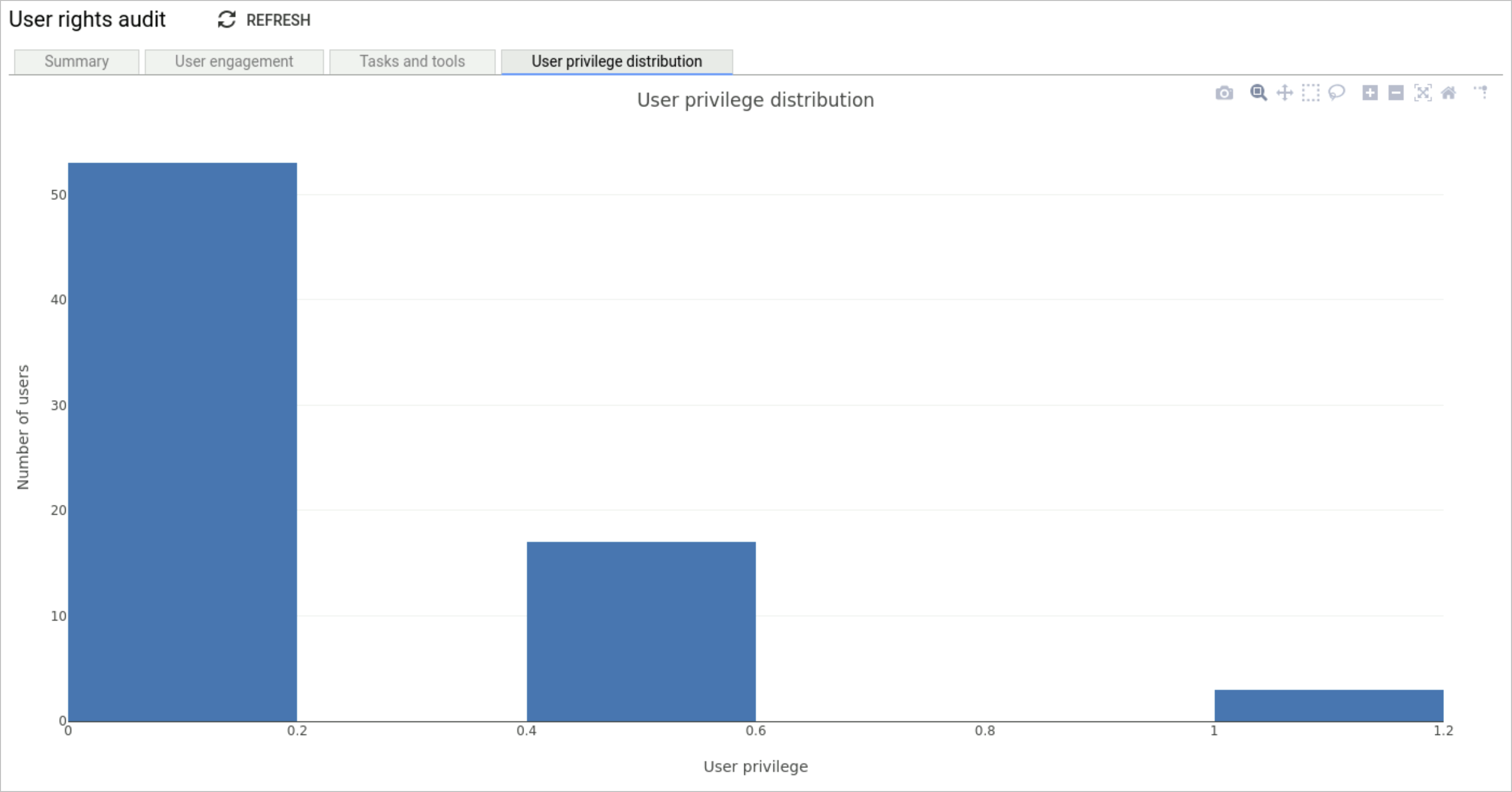
User privilege distribution
User privilege is a measure of how much coverage of a system a user has access to. It is a weighted sum of all the devices that a user has access to divided by the total number of devices in Osirium PAM device estate.
The weighting is calculated by the numerical level given in the device templates. In the device templates it is used to order the types of Fully Managed accounts by access level. Here it's used to calculate relative privilege levels.
Users given access by Password known or Password Management accounts are counted as having the highest possible privilege level for the device. Privilege can't be outside of 0 and 1.
Members of the Owner and Admin role are automatically given a privilege of 1.
The histogram shows how many users fall into various ranges of privilege levels.
Example:
- There are 3 devices in a system.
- A user has access to 2 of these.
- This user has access to one Password Management account and one Fully Managed account on different devices.
- The template that lists the Fully Managed accounts has admin with a level of 100 and read only with a level of 50.
- The user's Fully Managed account is read only.
Therefore, the user has a privilege level of 0.5.
(Number of Password known and Password managed accounts + ( user access level / max access level )) / number of devices
( 1 + (50 / 100) ) / 3 = 0.5
The template library has now been updated so that all the levels are more representative of the level of control over the devices that people actually have. Admin is 100, read only is 10 and anything else usually falls between levels 40 and 70.