Domain Service Accounts Report
This task will:
- Audit services from Windows servers found in Active Directory
- Find which services use a domain account
- Audit each domain service account from Active Directory
- Report on passwords that are old, expired, or approaching expiry
Playbook Files
Running this Playbook
- Click download playbook
- Import the downloaded file via the Playbooks page on PPA
- Build the playbook from the Edit & Build tab
- Run the playbook from the Preview & Deploy tab
Integrations
- PPA User Interface
- Hashicorp Vault Key-Value engine
- Windows Server Domain & Services
- Active Directory Domain, Computers & Users
Domain Maximum Password Age
This task uses the maximum password age configured in Active Directory to calculate password expiries.
If there is no maximum password age configured, a minimal report will be generated instead.
Required Vault Details
Active Directory
- IP/DNS address of a Domain Controller
- Domain FQDN
- Username
- Password
The Active Directory credentials require the permission to audit services on domain servers, & users in Active Directory.
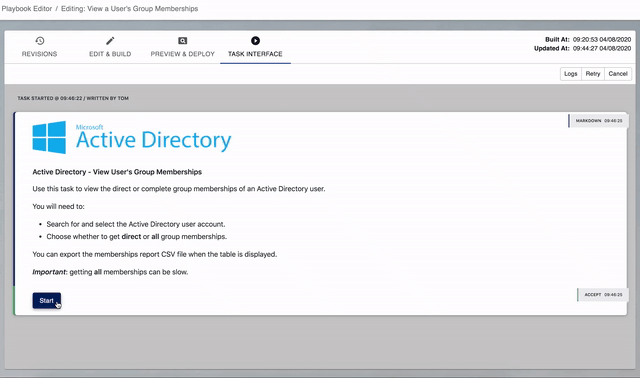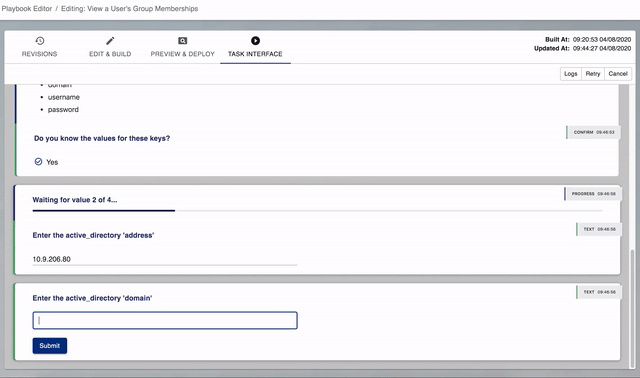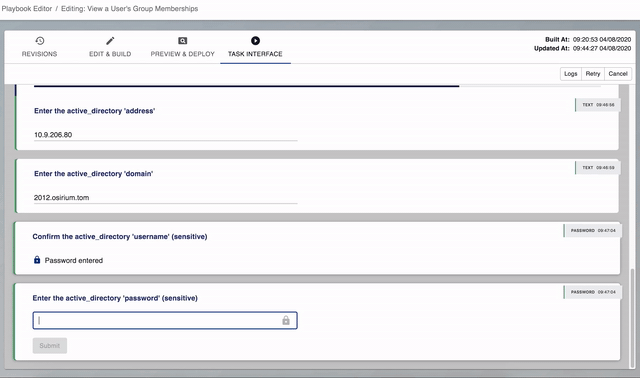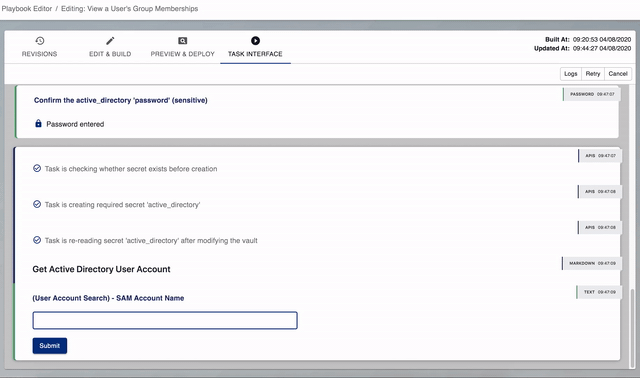
Vault Configuration Wizard
The first time you run a task built from this playbook, PPA will check the required Vault details exist.
If they don't exist, PPA will ask you to supply the details at the start of the task.
Below you can see a user providing details the first time they run an Active Directory task.
Once the details are added to Vault, the task won't ask for them again.
If you don't know the required details, ask an administrator to run the task or configure Vault manually.
What the Task Does
Once started, this task will:
- Find all servers in Active Directory
- Allow the Task Operator to select one or more servers
- Audit services that use a domain account from each server
- Check the password health of each service account in Active Directory
- Present a summary of password health & ask the task operator which accounts to display
Powershell Remoting (WinRM)
This task uses Powershell Remoting over WinRM to connect to Windows Servers & audit services.
See this Microsoft article for more information on how to securely enable WinRM.
Connection Settings
By default this playbook will:
- Use SSL when connecting to the Windows server
- Validate the Windows server certificate
You can change these settings on lines 10 & 11 of the playbook:
use_ssl: true
validate_cert: true
Get PPA for free!
Start automating your estate with a free 30 day trial today. No signup required!
Get PPA ExpressDocumentation
Installation Guide
See how easy it is to get started with our installation guide
Playbooks
View our task writing reference guide
Plugins
See how to integrate with different systems using our plugins reference guide.