Managing Active Directory
This section describes how an Active Directory can be setup to be used as a user account source for users logging into Osirium PAM. The following topics are covered:
- Active Directory integration in Osirium PAM
- Adding an Active Directory
- Active Directory named page
- Deleting an Active Directory
Active Directory integration in Osirium PAM
Active Directory can be integrated into Osirium PAM to enable your users to log onto the UI using their existing Active Directory user credentials.
Only a single Active Directory can be selected as the user authentication service.
To integrate Active Directory users we recommend you create user groups with an Active Directory source. This will allow you to synchronise all users in your Active Directory global security group with users in your Osirium PAM. Any users that don't already exist will be automatically created.
Note
For more information, see User Groups.
Active Directory authentication service can also be used to manage accounts used for outbound device connections and tasks as well as provision Active Directory member devices.
Adding an Active Directory
An Active Directory Service must be added before the following functionality can be used:
- Active Directory user group synchronisation.
- Active Directory authentication into PAM.
- Management of Active Directory accounts.
- Provisioning Active Directory devices.
To add an Active Directory Service:
-
In the left-hand menu click Active Directory :
-
Within the Manage Active Directory page click

NEW ACTIVE DIRECTORY. -
Within the New Active Directory window fill in the configuration information for your Active Directory service.
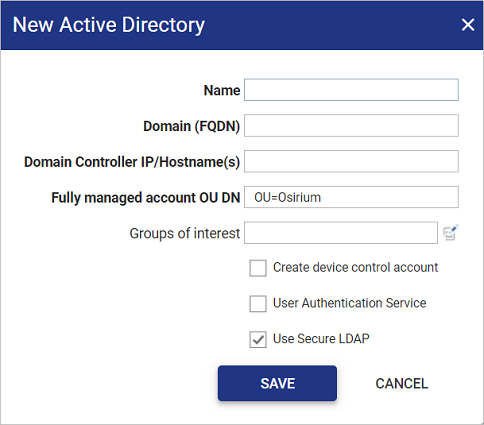
Field Name Description Name The Name will be used internally to reference the Active Directory. Domain (FQDN) Enter the fully qualified domain name of your Active Directory. The domain name will be used with a valid username/password to authenticate and provision the Active Directory.
Domain Controller IP/Hostname(s) Enter the IP / hostname of the Domain Controllers with Active Directory configured. Multiple Domain Controllers IP / hostname(s) can be entered by comma separating them within the field.
Fully managed account OU DN For deployments where the PAM Server should be able to create, delete, and manage the passwords and permissions of Active Directory accounts, the Active Directory should be provisioned using a set of Domain Admin credentials. In this type of deployment, the PAM Server will create an Organizational Unit (OU) in which to do this account and group management.
If the container input field is given a name, for example Management Accounts, then the OU that gets created will be called Management Accounts and will be placed in the root of the Active Directory.
By default, the container name is OU=Osirium. The container is created in the root of the Active Directory.
If the container needs to be placed inside another (or multiple) parent OUs then a DN can be specified to define where to add the PAM Server OU. For example, for the PAM Server to create an OU called Management Accounts inside a parent OU called Management Tools then use the following:
OU=Management Accounts, OU=Management Tools
For deployments where the PAM Server does not need to manage accounts in this way, the Active Directory can be provisioned with Domain User permissions. In this case, no OU will be created and any data in this field will be ignored.
NOTE The reverse order of OUs in the DN. Do not include any Domain Component attributes (DCs). All parent OUs must already exist, the PAM Server does not create any parent OUs.
Groups of interest The Active Directory group(s) that should be audited by the PAM Server. This field is useful to narrow down the auditing of accounts to those that have high levels of privileges and may pose a security risk. NOTE If this field is left blank, all users from the Domain Users group will be audited.
In the Edit value window, click the
Newdrop-down and select
Add entry. A new value field will appear in the table. Add the name of the group you want to be audited. The group name entered must match the name of the group on the Active Directory server.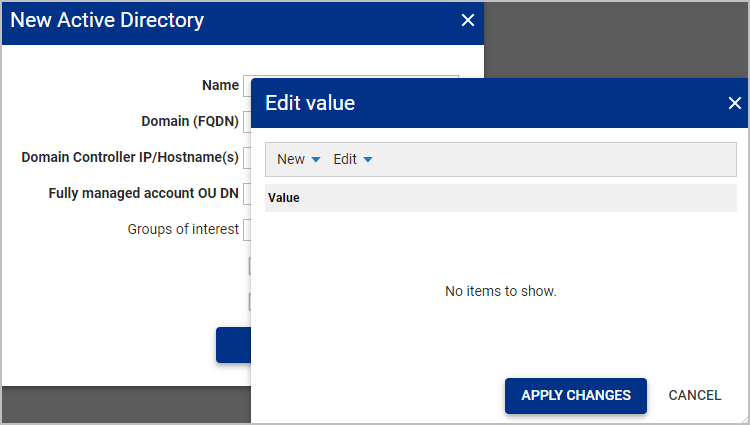
Multiple groups can be added by selectingNew >
Add entry again.Groups of interest can be removed from the Active Directory, but doing so will make any accounts that are only members of the removed group invisible to Osirium PAM after the next Active Directory audit. The records for these accounts will no longer be visible in the Active Directory accounts view.
If any of these accounts were in a Known or Managed state, you will lose the ability to:
- Use these accounts as control accounts.
- Use them as access levels in a profile.
- Reveal/manage the credentials of the accounts.
- View their credentials in a new Breakglass report.For this reason we do not recommend removing a group of interest until all accounts in that group are set to either an approved or unapproved state.
Create device control account If the checkbox is ticked, the PAM Server will create a device access account to manage any member servers provisioned as Fully managed. The device access account is named osirium_deviceaccess_account.
It is located in the Osirium OU, Users OU.Alternatively, if you want to switch a Known or Managed member servers to Fully managed, you should select this account as the device's control account.
If you don’t create the PAM Server control account at this time then it can be created another time through the Manage accounts > Active Directory accounts tab and clicking
Create accountbutton.User Authentication Service Select whether this Active Directory should be used for both inbound Active Directory user authentication. NOTE Only one Active Directory service can be selected as the user authentication service.
Before clicking
Yestake note of the following. If you already have another Active Directory service selected as the User Authentication Service, choosing a new User Authentication Service may affect existing Active Directory user authentication into the PAM UI.Use Secure LDAP Default is enabled. Select whether this Active Directory should use secure LDAP (LDAPS) or standard LDAP. -
Click
SAVE. -
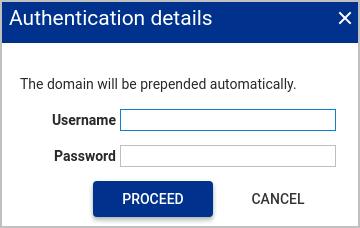
Within the Authentication details window enter a valid Username and Password.
Note
If you are using Groups of interest then the username/password used to authenticate the Active Directory must exist in one of the groups added.
-
Click
PROCEED.A number of tasks are run by the PAM Server to provision and audit the Active Directory.
If the Create device control account checkbox was ticked, the Create device control account task will be run to create the osirium_deviceaccess_account. This account is created in Osirium > Admins OU in Active Directory.
The osirium_deviceaccess_account will be seen on the Manage accounts > Authentication Service accounts tab and will be linked to the PAM Server.
Active Directory named page
The Active Directory detail page provides information relating to the Active Directory service, and allows you to administer the Active Directory and it's accounts.
To view the Active Directory detail page, click on its name in the table.
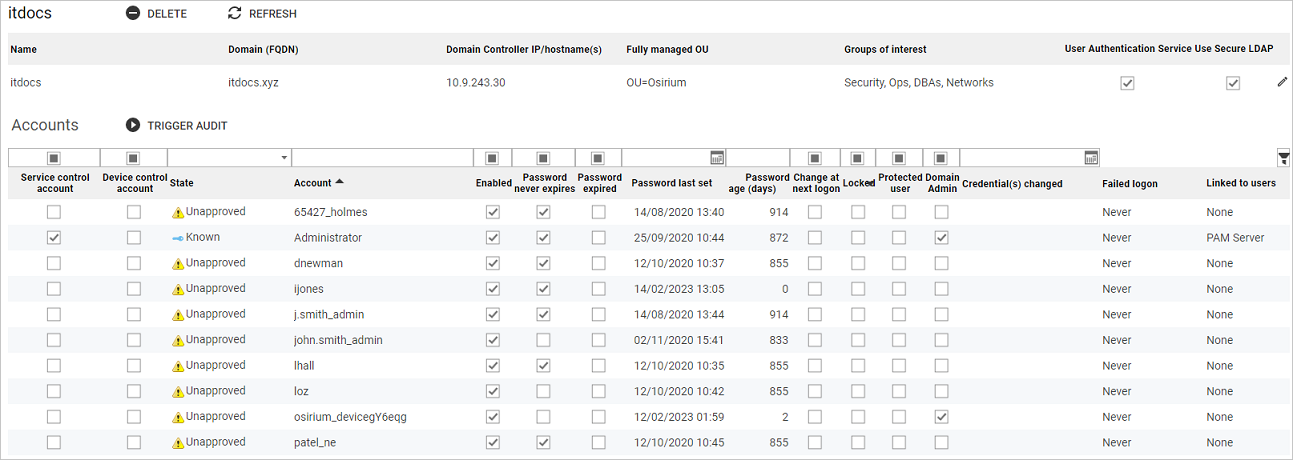
The following administrative tasks can be carried out on this page:
| Action | Description |
|---|---|
| Name | Change the name you reference your Active Directory within Osirium PAM. |
| Domain Controller IP/hostname(s) | Change or add multiple Active Directory Domain Controllers IP/hostname(s). Multiple entries should be separated by a comma to separate them. |
| Groups of interest | Enables you to add further groups of interest, Active Directory groups with high levels of privilege that may, therefore, pose a greater security risk. Any changes made will trigger an automatic audit on the Active Directory service. |
| User Authentication Service | Enable to use the Active Directory for inbound user authentication to the UI. NOTE Only one Active Directory service can be selected as the user authentication service. |
| Trigger audit | See Trigger Audit Button. |
The accounts section displays all the accounts that exist on the Active Directory.
The information presented in the table includes:
| Heading | Description |
|---|---|
| Service control account | If discovered, will be marked with a  and used by Osirium PAM to: and used by Osirium PAM to:- Create and delete Osirium PAM accounts/groups on the Active Directory Service. - Refresh passwords on the Active Directory. |
| Device control account | Will be marked with a  and used by Osirium PAM to run tasks on the member servers. and used by Osirium PAM to run tasks on the member servers. |
| State | A State is set for each of the accounts discovered when a DeviceAudit task is run. |
| Account | Name of the account that exists on the Active Directory. |
| Enabled | If marked with a  the account is enabled in Active Directory. the account is enabled in Active Directory. |
| Password never expires | If marked with a  the Active Directory password will never expire. the Active Directory password will never expire. |
| Password expired | If marked with a  the Active Directory password has expired and must be reset in Active Directory. the Active Directory password has expired and must be reset in Active Directory. |
| Password last set | Timestamp of when the Active Directory password was last set. |
| Password age (days) | The number of days since the Active Directory password was last set. |
| Change at next logon | If marked with a  the user will be prompted to change the account password when they next login to their workstation via Active Directory. the user will be prompted to change the account password when they next login to their workstation via Active Directory. |
| Locked | If marked with a  the account has been locked in Active Directory. the account has been locked in Active Directory. |
| Protected user | If marked with a  the account is a member of the Protected Users group in Active Directory. the account is a member of the Protected Users group in Active Directory. |
| Domain Admin | If marked with a  the account is a member of the Domain Admins group in Active Directory. the account is a member of the Domain Admins group in Active Directory. |
| Credential(s) changed | Timestamp of when the account credential(s) were last changed. |
| Failed logon | Timestamp of the last failed logon attempt made when the account is used to connect to Active Directory or device through Osirium PAM. |
| Linked to users | Osirium PAM user to which the account is linked. |
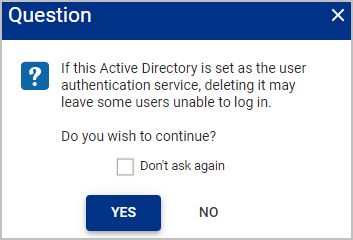
Deleting an Active Directory
An Active Directory service cannot be removed if it is being used by member servers. All member servers will need to be unprovisioned before deleting the Active Directory.
To delete an Active Directory:
-
In the left-hand menu, click on
Active Directory. -
On the Manage Active Directory page, right-click on the Active Directory to be removed and select

Deletefrom the context menu. -
Within the Question window, click
YES, if you are sure you want to delete the Active Directory. If there is no other Active Directory authentication service set, then users that require an Active Directory to authenticate will no longer be able to login into Osirium PAM.