Upgrading from a Standalone PAM to PAM HA Pair
This section looks at how to upgrade from an existing standalone PAM Server to a PAM HA Pair configuration.
Prerequisites
Before you can configure a PAM HA Pair you will need the following prerequisites:
| Prerequisite | Description |
|---|---|
| Upgrade path | Review the Upgrade paths to ensure you are applying the correct upgrade method based on the version you are upgrading from and to. |
| Hardware and Software | Ensure the correct resources are available before upgrading. The following outlines the hardware and software requirements.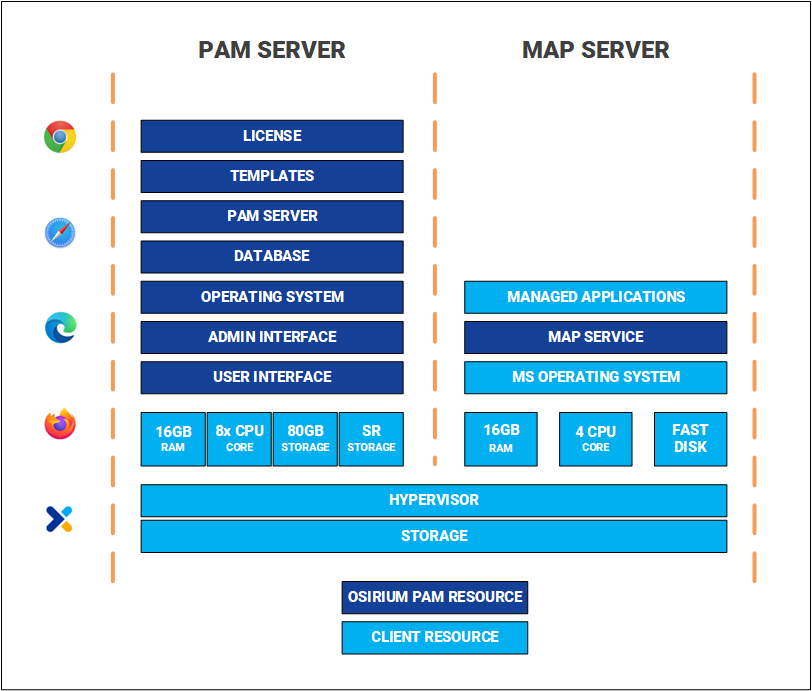 |
| Software downloads | Download the latest upgrade kit click here. |
| Disk space | Ensure the internal disk has a minimum of 5GB free disk space. |
| Recent backup | We recommend that you have a recent Osirium backup as well as VM Level backup or Snapshot of the standalone PAM Server being upgraded. |
| No active user connections | Ensure there are no active user connections. |
| Disable Task 'Regenerate Account Credentials for all devices' | Within the Admin Interface, disable all scheduled Regenerate Account Credentials for all devices tasks within profiles. |
| Osirium Support account | Within the Admin Interface ensure the Osirium Support account has been enabled and a password set. |
| .local DNS domains | If you are using .local DNS domains, ensure matching records have been entered in the DNS Search Suffixes. |
We also recommend the following:
| Prerequisite | Description |
|---|---|
| SMB filestore | RECOMMENDED Configure an SMB filestore to store Session Recording files. For instructions click here SMB Filestore. |
| Floating IP address | RECOMMENDED Allocating a floating ip address will allow the ip address to be dynamically assigned to the active PAM Server. This means the user will only need a single ip address when connecting to PAM and not have to switch ip addresses if a failure occurs. |
Upgrade procedure
The diagram provides a high-level overview of the process for upgrading a standalone PAM Server to a PAM HA Pair configuration.
Standalone to PAM HA Pair upgrade procedure flowchart
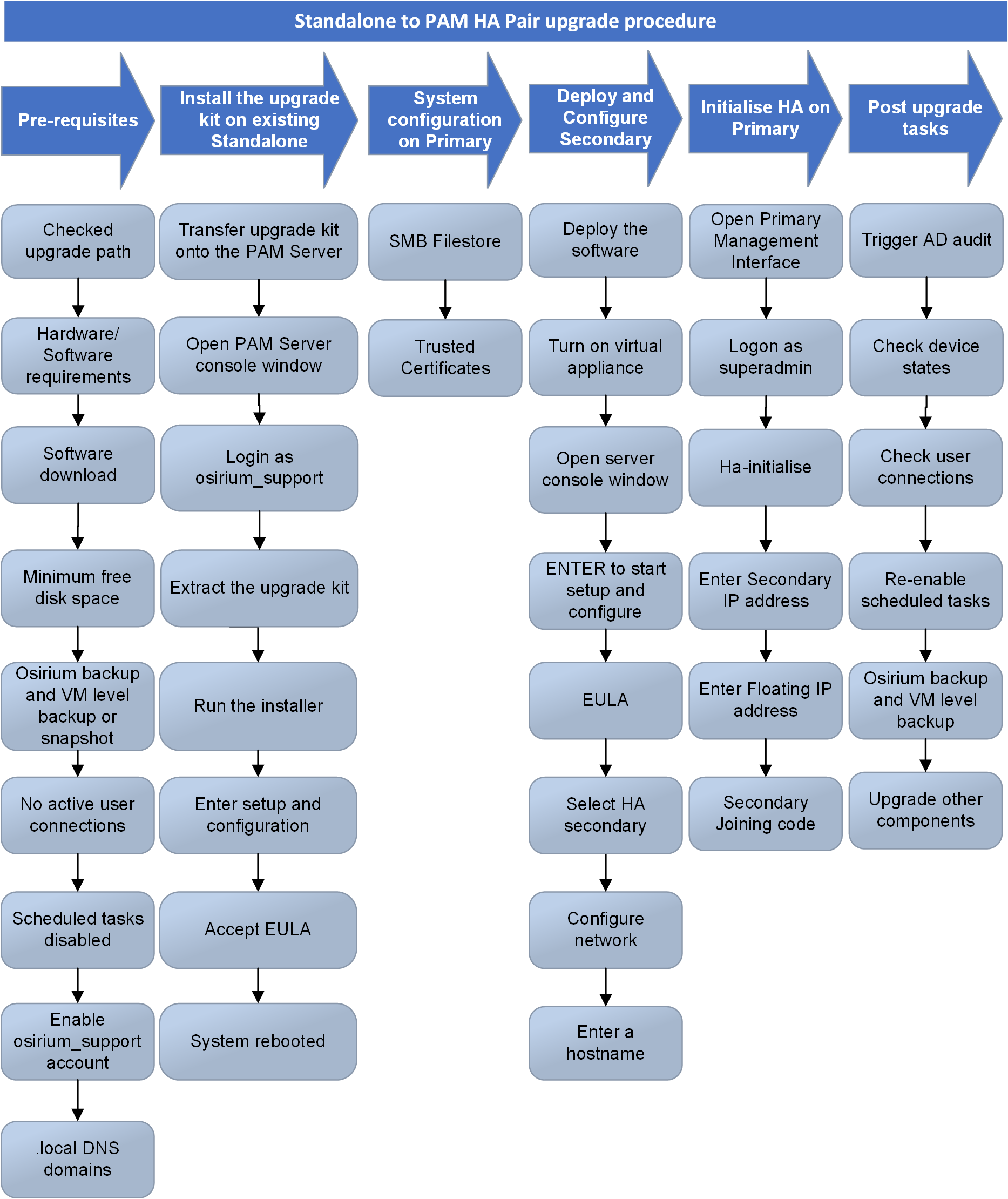
Upgrade steps
- Upgrade the Standalone PAM Server
- System Configuration
- Deploy the Secondary PAM Server
- Configure a Secondary PAM Server
- Initialise High Availability
Upgrading the Standalone PAM Server
-
Open a file transfer tool of your preference and copy the upgrade kit onto the standalone PAM Server using the osirium_support account.
-
Open the PAM Server Console window, then press ALT + F2. The server login prompt appears.
Note
Alternatively, you could use an SSH connection to the PAM Server.
-
Enter osirium_support at the login prompt and press ENTER.
-
When prompted, enter the password of the osirium_support account and press ENTER.
-
Extract the upgrade kit copied to the server using the following command:
sudo bash Osirium_PAM_Server_vA.B.C_upgrade.binWhere A.B.C is the version you are upgrading to.
-
Enter the osirium_support account password when prompted and press ENTER.
-
When the kit has been extracted, type the command specified on the screen and press ENTER.
-
Press ENTER when prompted to start the setup and configuration.
-
The EULA screen will be displayed. Press ENTER once you have read it.
-
Wait while the upgrade completes and the server is rebooted.
System Configuration
The following system configuration steps are required on the upgraded PAM Server:
SMB Filestore RECOMMENDED
We highly recommend that an SMB filestore is configured to maintain resilience and ensure session recordings continue to be available in case of any failovers.
Warning
If an SMB filestore is not configured then you are at risk of losing files stored locally on the PAM Server.
To configure:
-
Within the Admin Interface navigate to the System configuration > System settings tab.
-
Click on the
 next to SMB share configuration.
next to SMB share configuration. -
Enter the SMB share details.
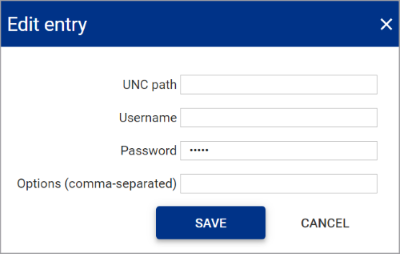
Field name Description UNC path The UNC path by which PAM can connect to the SMB share. For example \server-name\shared-resource-pathname
Username The username of the SMB share location. Password The password of the SMB share location. Options (comma-separated) Optional
Allows additional parameters to be passed to the SMB share as a comma separated list if required. -
Click
SAVE. -
Click on the
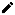 next to File store.
next to File store. -
Select SMB Share and click
SAVE.
Uploading a trusted certificate RECOMMENDED
By default, Osirium PAM provides a generic certificate to allow secure web connections to the UI and Admin Interface.
We recommend that you upload a trusted certificate valid within your organisation. For further details on the types of certificates that can be uploaded click here.
The steps to upload a certificate differ depending upon the certificate type.
Certificate with RSA private key
To upload:
-
Within the Admin Interface navigate to the System configuration > Certificates tab.
-
On the Certificates tab, click LOAD NEW CERTIFICATE.
-
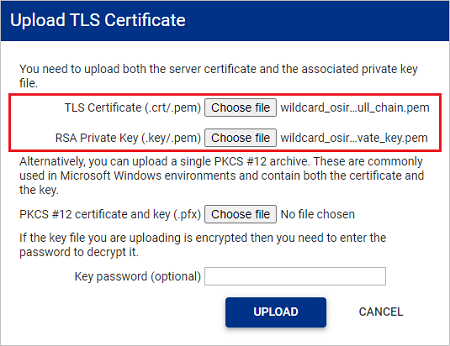
In the Upload TLS Certificate window, upload your trusted certificate and RSA private key. Both are required for a successful upload.
- TLS Certificate: Uploaded certificates will be verified to ensure they are an X.509 certificate with a .pem file format.
- RSA Private Key: Uploaded keys are verified to ensure they are an rsa key with a .key file format. Passwords/passphrase are NOT supported on the the rsa key.
-
If the private key you are uploading has been encrypted, enter the password in the Key password (optional) input box.
-
Click UPLOAD. The certificate is uploaded.
PKCS12 archive file
To upload:
-
Within the Admin Interface navigate to the System configuration > Certificates tab.
-
On the Certificates tab, click LOAD NEW CERTIFICATE.
-
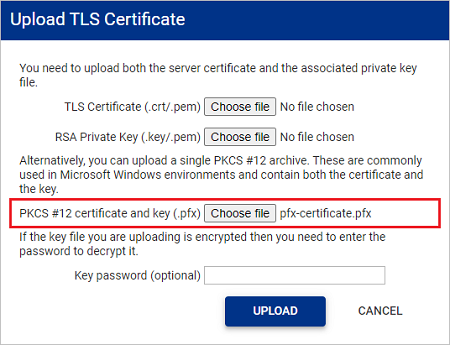
In the Upload TLS Certificate window, upload your PKCS #12 file.
- The certificate contained within the PKCS #12 file will be verified to ensure it is a X.509 certificate.
- The private key contained within the PKCS #12 file will be verified to ensure it is an rsa key.
-
If the private key you are uploading has been encrypted, enter the password in the Key password (optional) input box.
-
Click UPLOAD. The certificate is uploaded.
Deploy the Secondary PAM Server
To create the HA Pair you will need to create a Secondary PAM Server. Deploy the software package into your chosen supported infrastructure. Click on the appropriate link below to be navigated to the deployment steps.
- Deploy using VMware vSphere
- Deploy using Microsoft Azure
- Deploy using Microsoft Hyper-V
- Deploy using Amazon Web Services
- Deploy using Nutanix Prism Central
Configure a Secondary PAM Server
Follow these configuration steps if you are setting up a new Secondary PAM Server.
-
Within the Console window, press ENTER when prompted to start the setup and configuration.
-
Read and accept the EULA to continue.
-
Select HA secondary (or replacement primary) as the installation type.
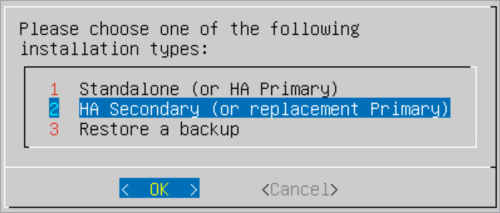
-
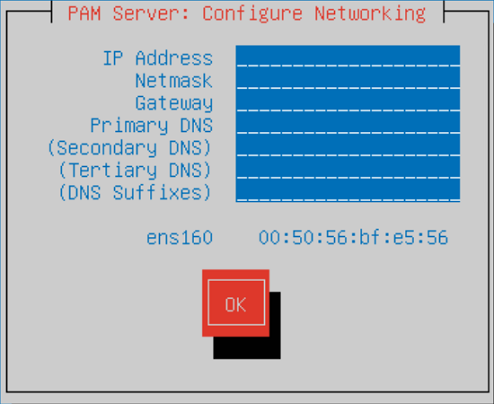
Within the Configure Networking screen, configure the following server settings. Press TAB to navigate between the fields.
- IP Address: Enter the IP Address which will be used to connect to the server.
- Netmask: Enter the network mask.
- Gateway: Enter the network default gateway IP address.
- Primary DNS: Enter the network primary DNS IP address.
- (Secondary DNS): Enter the secondary DNS IP address if relevant, else leave blank.
- (Tertiary DNS): Enter the tertiary DNS IP address if relevant, else leave blank.
- (DNS Suffixes): Enter the DNS Suffixes. Multiple entries can be separated with a comma, else leave blank.
-
Once completed TAB down to the
OKbutton and press ENTER. -
Within the Enter a hostname window, enter a name to identify the new server.
-
TAB down to the
OKbutton and press ENTER. -
Once the setup has completed a message will be displayed. Your system is now ready for High Availability.
Make a note of the joining code displayed on the screen as it will be required to initialise your PAM HA pair.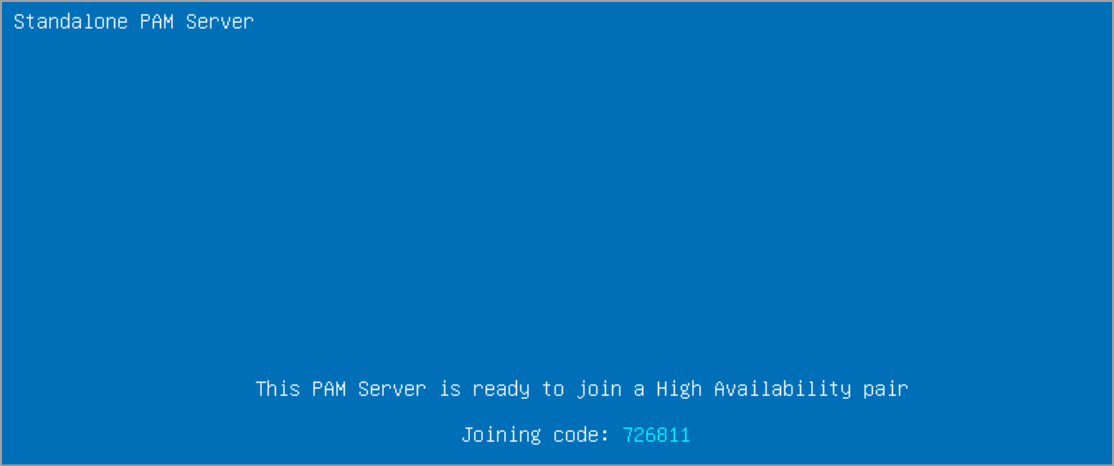
Initialise High Availability
Once you have upgraded your standalone PAM Server and deployed and configured your Secondary PAM Servers, the final step is to initialise your HA pair and setup replication.
-
Open up a web browser and enter the address of the Primary PAM Server:
[PAM Server Address]:8443You will be presented with the PAM Management Interface.
-
Login with a username and password.
Note
PAM user must belong to the PAM Owner group that gives them Owner role level access to PAM.

-
You will be presented with PAM Management Interface SSH window.
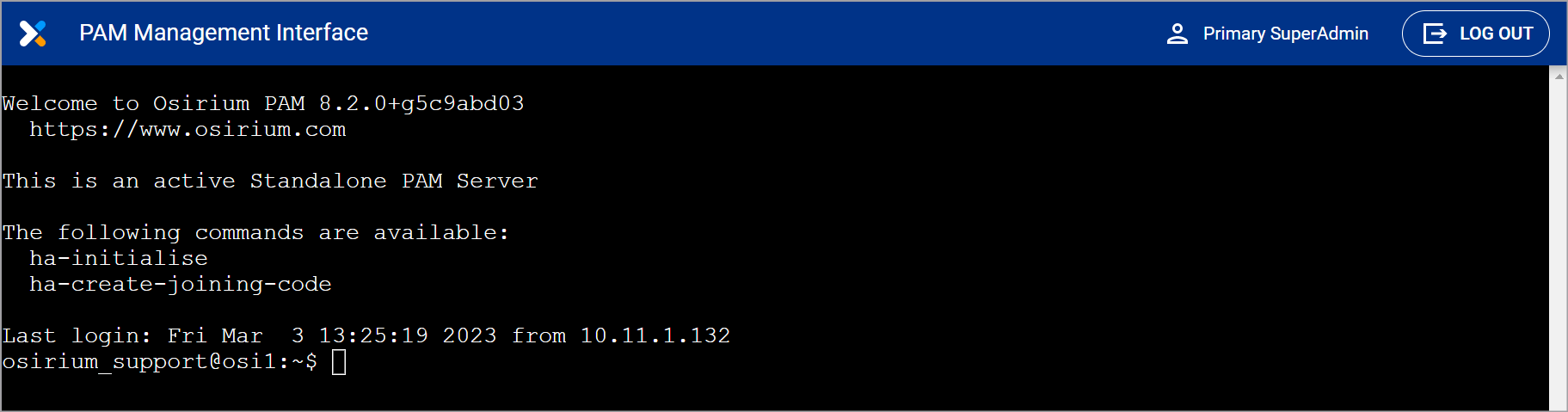
-
At the prompt type ha-initialise and press ENTER.
Note
If you don't have an SMB filestore configured you will be prompted with a warning. We recommend an SMB filestore is configured before continuing.
-
Enter the IP address of the Secondary PAM Server and press ENTER.
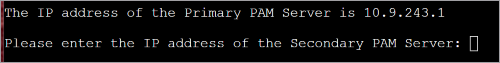
-
Enter a floating IP address and press ENTER.
-
Read what will happen on the secondary then type y and press ENTER to continue.
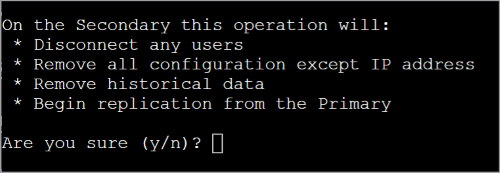
-
Enter the joining code of your Secondary PAM Server which can be found on the server console window and press ENTER.

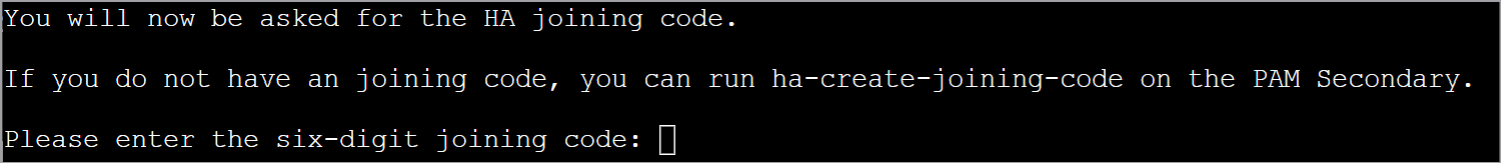
-
Wait while the joining procedure completes.
-
When the operation has completed, you will be asked to confirm you can connect to the Management Interface of the Secondary PAM Server . Follow the instructions on screen and log in using the superadmin username and password set on the Primary PAM Server during configuration.
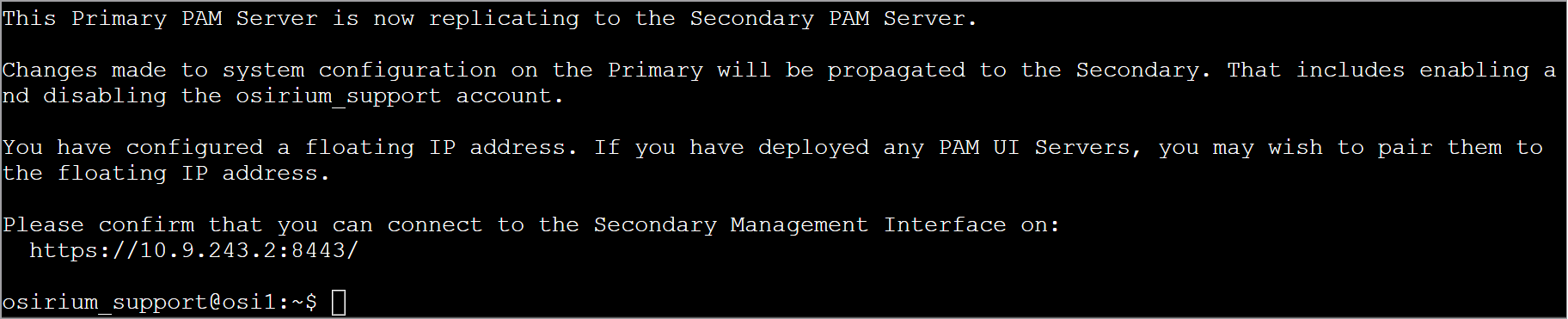
The message on the Secondary PAM Server console window will also change and state the PAM Server is in standby.
HA Pair configuration is now complete.
Post upgrade tasks
Once the PAM Server upgrade to a HA Pair has successfully completed, log on to the Primary PAM Server and check the following before allowing users to reconnect:
| Post upgrade task | Description |
|---|---|
| Trigger AD audit | Before opening any device connections that use an Active Directory account, an audit needs to be manually triggered on all provisioned Active Directories. You can do this by right clicking the Active Directory on the Manage Active Directory page, and select Trigger audit from the menu. |
| Check device states | Check device status to ensure they are running successfully. |
| Check user connections | Check users can connect to devices. |
| Re-enable scheduled tasks | Re-enable scheduled Regenerate Account Credentials for all devices tasks. |
| Backup | Take an Osirium backup as well as VM Level backup of both the HA Pair PAM Servers. |
| Upgrade PAM UI | If you are using a standalone PAM UI Server then use the PAM Component Compatibility Matrix to check if the PAM UI Server needs updating inline with the PAM version you have upgraded to. Upgrade as appropriate. |
| Upgrade MAP Server | If you are using a MAP Server then use the PAM Component Compatibility Matrix to check if the MAP Server needs updating inline with the PAM version you have upgraded to. Upgrade as appropriate. |