Reinstating a failed PAM Server
This section details the process required to restore a failed standalone PAM Server. It also outlines the different process available to restore a cluster.
Restoring a standalone PAM Server
If you have a standalone deployment then the following steps will apply to restoring your PAM Server.
- Prerequisites
- Restore a standalone PAM Server procedure
- Deploying the PAM Server
- Steps to restoring the PAM Server
- Post restore tasks
Prerequisites
Before starting your restore make sure the following prerequisites are met:
| Prerequisite | Description |
|---|---|
| Recent Osirium backup file | Ensure the Osirium backup file is available and accessible. See Data and Configuration backup for more information on backup file requirements. |
| Ports | Ensure TCP ports 443 and 9002 are open as they are required for the PAM UI and PAM Client. TCP 2380 (etcd, i.e. key-value store), 2390 (cluster setup API), 2391 (cluster delegation API), 5432 (postgres, i.e. database) For a full list of ports used by the server click here . |
| Master Encryption Key | Ensure you have the Master Encryption Key (MEK) of the PAM Server you are restoring. |
| Unmount external drives | If you have any external drives configured then unmount from the existing server. |
| Hardware & Software | Ensure the correct resources are available before deploying. The following outlines the hardware and software requirements.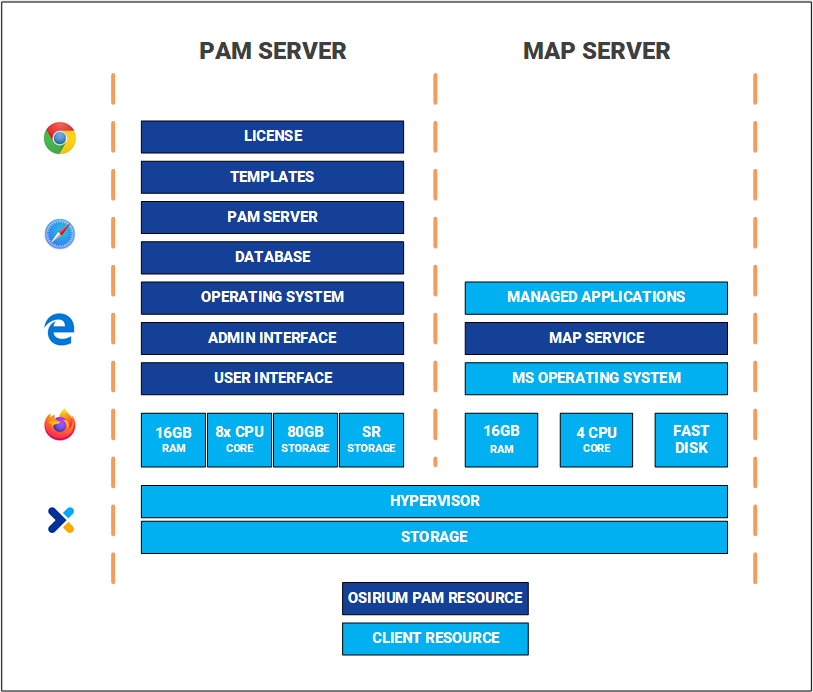 |
| Software downloads | Download the Osirium PAM version you want to restore onto. To download the latest PAM Server software release package for deployment into your infrastructure, click here. To download earlier versions of the PAM Server software packages, please contact Osirium support by clicking here. |
Restore a standalone PAM Server procedure
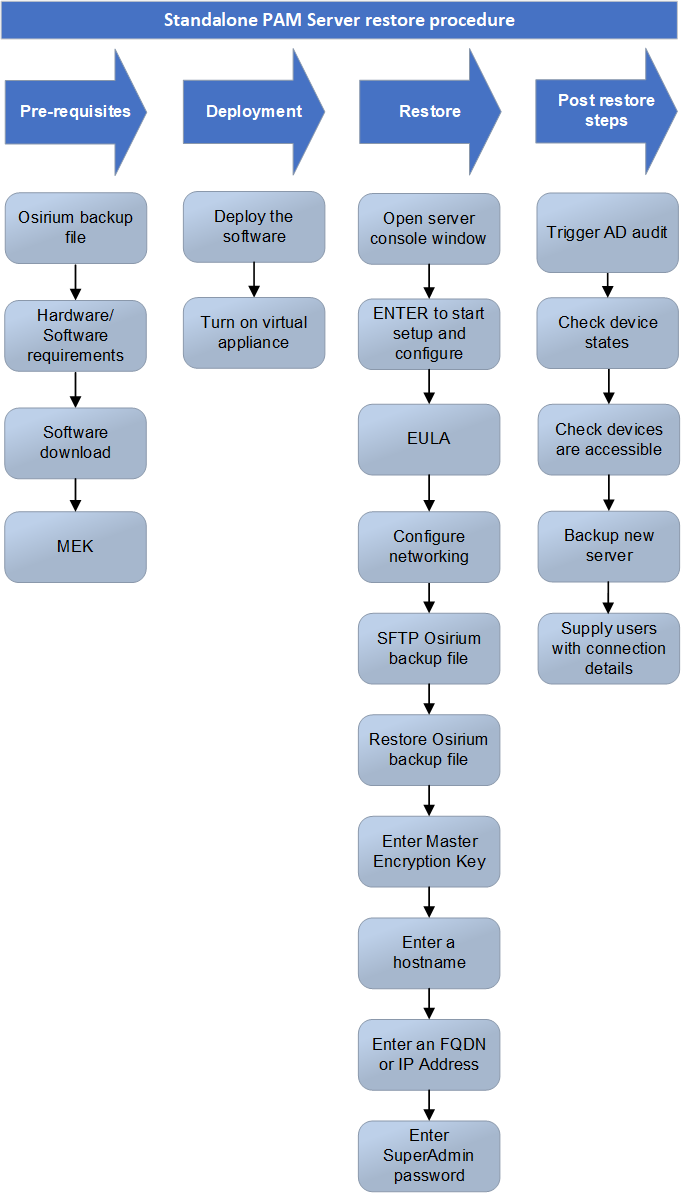
The diagram provides a high-level overview of the process for restoring a standalone PAM Server.
Standalone PAM Server restore procedure flowchart
Deploying the PAM Server
You will firstly need to deploy a new PAM Server to install your Osirium backup file onto.
Deployment into the different supported infrastructures may vary, therefore click on a link below to be navigated to the correct deployment steps.
- Deploy using VMWare vSphere
- Deploy using Microsoft Azure
- Deploy using Microsoft Hyper-V
- Deploy using Amazon Web Services
Steps to restoring the PAM Server
-
Open the console window of the new PAM Server.
-
Within the Console window, press ENTER when prompted to start the setup and configuration.
-
Read and accept the EULA to continue.
-
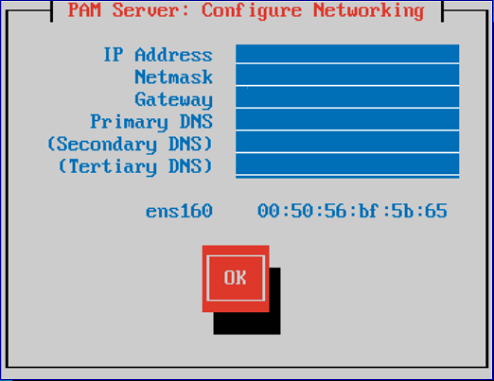
Within the Configure Networking screen, configure the following server settings. Press TAB to navigate between the fields.
- IP Address: Enter the IP Address which will be used to connect to the server.
- Netmask: Enter the network mask.
- Gateway: Enter the network default gateway IP address.
- Primary DNS: Enter the network primary DNS IP address.
- (Secondary DNS): Enter the secondary DNS IP address if relevant, else leave blank.
-
Once completed TAB down to the
OKbutton and press ENTER. -
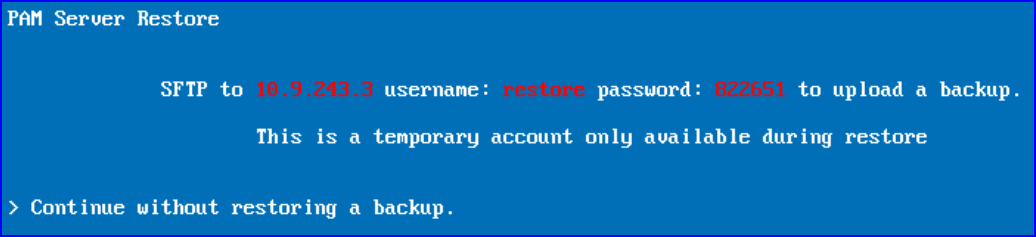
When you get to the PAM Server Restore screen, SFTP onto the virtual appliance using the details shown on the screen.
-
Copy the Osirium backup file of the PAM Server you want to restore. Once successfully copied, the screen will update and the copied Osirium backup file will appear in the list.
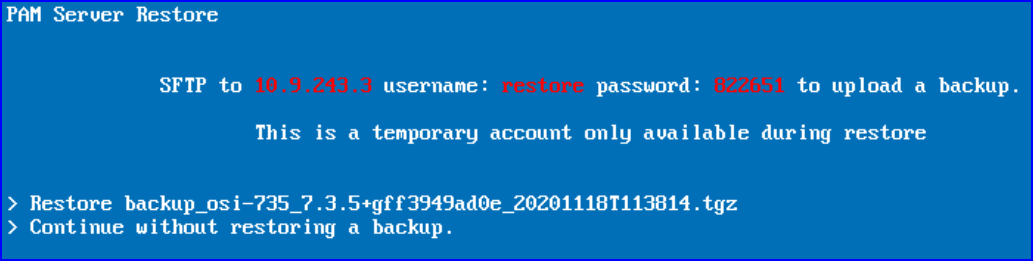
-
Select the Osirium backup file and press ENTER. When prompted TAB to the
OKbutton and press ENTER to confirm the restore. -
Enter the Master Encryption Key (including dashes) of the PAM Server that the backup was taken from. Select
OKand press ENTER.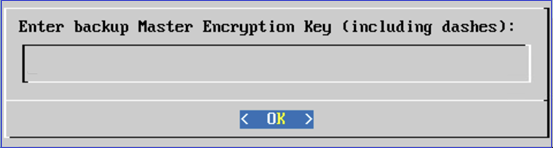
-
Within the Enter a hostname window, enter a name to identify the server.
-
TAB down to the
OKbutton and press ENTER. -
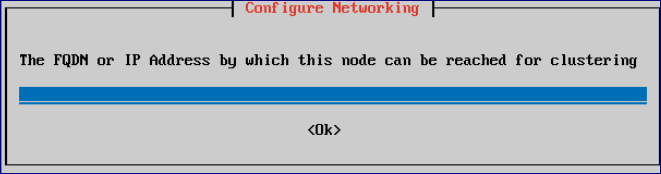
Enter the FQDN (all in lowercase) or IP Address which will be assigned.
Warning
If your Osirium PAM deployment will be using the Mesh functionality which allows the PAM Server to push a copy of its Osirium backup files to a secondary PAM Server, then you must enter an FQDN and NOT an IP Address.
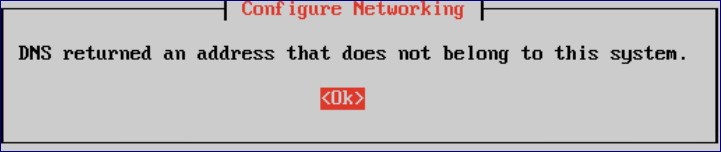
If the following error occurs then make sure that the hostname can be resolved and check if it has been included in the DNS A records - see Prerequisites.
-
TAB down to the
OKbutton and press ENTER. -
Set a password for the Primary SuperAdmin account. The username (SuperAdmin) and the password will be used later to log into the PAM UI.
-
TAB down to the
OKbutton and press TAB. -
Confirm the primary SuperAdmin account password.
-
TAB down to the
OKbutton and press TAB. Wait while the system is configured and restored with the backup file.Make a note of the https address which will be required to connect to the server via PAM.
Post restore tasks
Before allowing users to connect back onto the PAM Server:
-
Remount the external disk.
-
Before opening any device connections that use an Active Directory account, an audit needs to be manually triggered on all provisioned Active Directories. You can do this by right clicking the named Active Directory from the Manage Active Directory page, and select Trigger audit from the menu. This will allow additional fields on the Manage accounts> Active Directory accounts tab to be populated.
-
Ensure the devices are running successfully.
-
Ensure the devices are still accessible through the PAM interface.
-
Take an Osirium backup of the new PAM Server.
-
Supply users with new hostname connection details as they will have changed.
Restoring clustered deployments
If you have a clustered deployment then the restore method will depend on the backup strategy that you have adopted.