Account mappings
This section describes how to create patterns to map Osirium PAM user accounts to device accounts through profiles. The following topics are included in this section:
- Mapping accounts to pre-existing privileged accounts
- Trigger scan
- Creating an Account mapping
- Editing an account mapping
- Deleting an account mapping
Mapping accounts to pre-existing privileged accounts
Account mappings are a useful tool for organisations that have already created individual privileged accounts on devices for their users and want to continue using them.
When a mapping is created, the mapping pattern is applied to each Osirium PAM user and the resulting mapping is stored in the account mapping matrix. Once a username entry with the mapping applied has been created and listed in the matrix, the entry can be edited.
The application of mappings can help with the following scenarios:
- Active Directory naming conventions for which Osirium PAM has all the required information to apply a correct pattern.
- Active Directory naming conventions where Osirium PAM doesn't have all the information to apply a correct pattern.
- Users that need to be assigned an account from a pool of privileged accounts.
- Unique conventions that don't fit into just one mapping.
Once the mapping has been applied and the results stored in the matrix for each user, you will be able to create a profile to grant multiple users access to the device using the mapping as an access level.
For example:
-
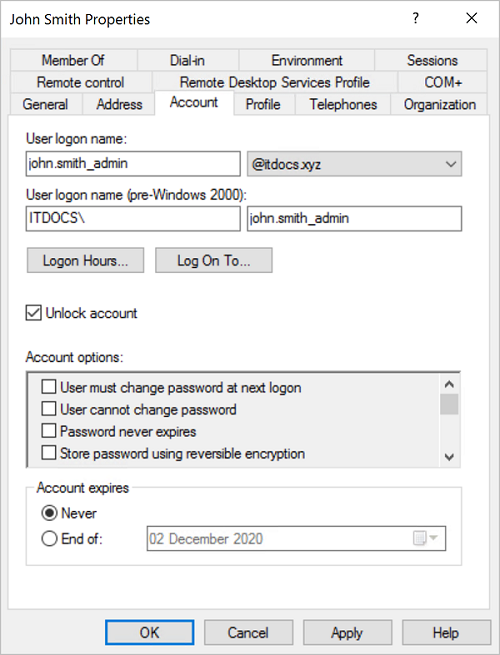
User account john.smith_admin already exists on the device.
-
Once this account is audited in Osirium PAM, in order to use it with an account mapping the state needs to be Known or Managed.
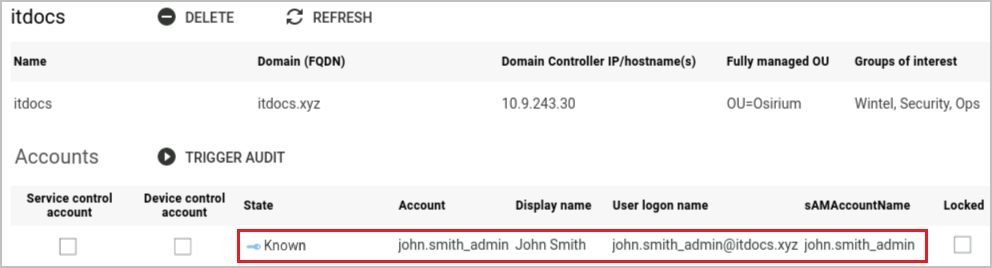
-
Within Osirium PAM the mapping is created as follows: %username%_admin.
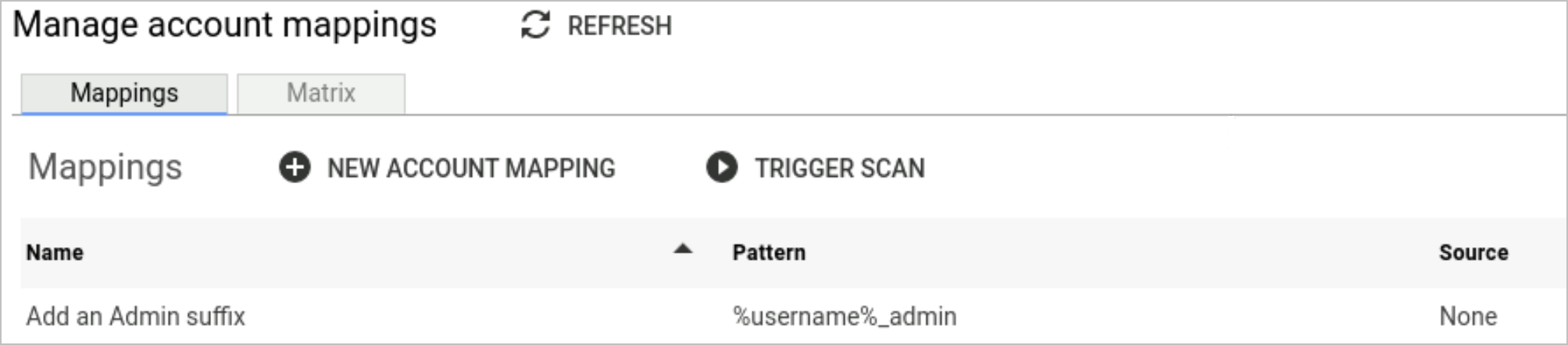
Along with an entry in the matrix.
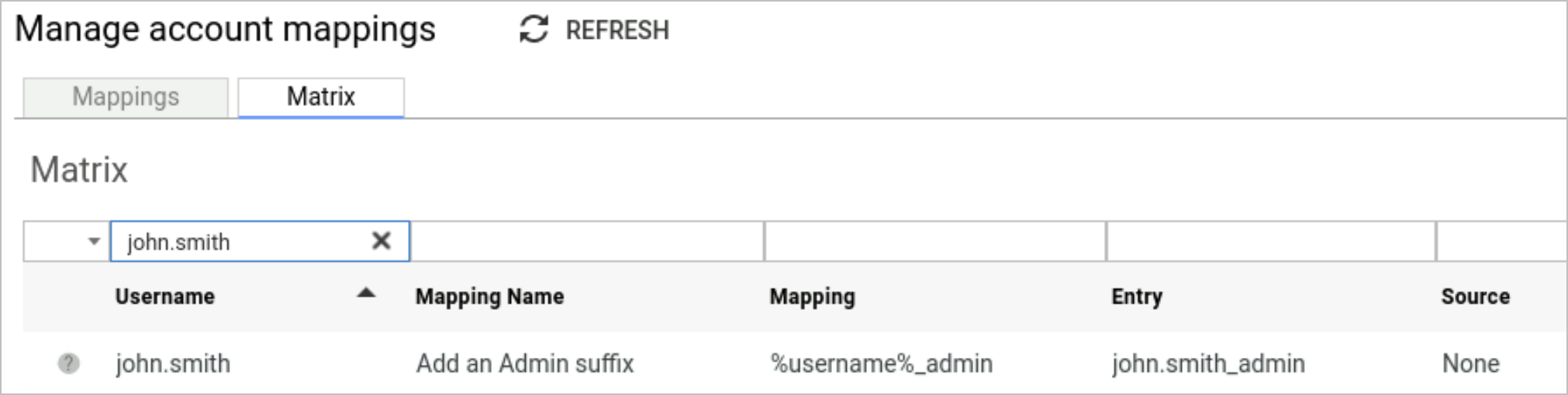
-
The mapping can then be selected within a profile:
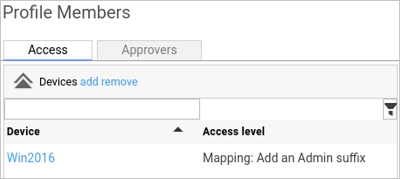
-
Osirium PAM user john.smith logs onto the UI.
-
From the UI the RDP tool is launched. Osirium PAM uses the users mapped username entry stored in the matrix (john.smith_admin) to log onto the device along with the known password.
Manage account mappings
The Manage account mappings page contains a Mappings and Matrix tab. The information contained in the tabs is as follows:
| Tab | Description |
|---|---|
| Mappings | Lists the account mappings that have been created and can be used. |
| Matrix | When an account mapping is created, it is used to create a mapping for each user which is then listed in the matrix. Users will have a mapping for each account mapping created. |
Trigger scan
Before you trigger a scan, a pattern must be selected. Triggering a scan, runs the MappedAccountScan task against the users/devices in the profile the account mapping has been used in. This task verifies if the appropriate account exists on the devices or account sources relevant to the profile.
The task will fail if expected mapped accounts are not found. View the log to find out which accounts weren't found on the device/authentication services.
Mappings tab
The mappings tab is used to store the mappings that are applied to the users to create the matrix entries.
The information presented on the Mappings tab includes:
| Heading | Description |
|---|---|
| Name | Internal name to identify the mapping and its purpose. |
| Pattern | The pattern which is applied to the Osirium PAM user to create the users mapped username which is stored in the matrix. This mapping can be selected as an access level within a profile. NOTE Mappings will be done with diacritic (accents added to words) insensitivity and case insensitivity. |
| Source | The source (i.e. Active Directory) that the account mapping will be linked. The source will be used to audit and check each account mapped entry in the matrix. If set to 'None' then no account source is available to audit against. |
| Notes | Any additional information relating to the mapping. |
| # Profiles | Total number of profiles the mapping is being used in. |

Creating an account mapping
Before creating account mappings consider the following cases and mapping substitutions available to help you understand what account mapping pattern you require.
Mapping substitutions
The first and last parts of mapping substitutions are determined as the text before and after the delimiter. Valid delimiters are dot (.) and underscore (_).
If we take the example username john.smith:
-
%username_first_1-20% : the first 1-20 characters of a username. For example %username_first_6% = john.s
-
%username% : the whole username as used by the user to log into the UI = john.smith
-
%first_initial% : the first character of the first part of the username = j
-
%first_part% : the whole of the first part of the username = john
-
%last_initial% : the first character of the second part of the username = s
-
%last_part% : the whole of the second part of the username = smith
-
%email_address% : the entire email address associated with the Osirium PAM user = john.smith@xyzcompany.com
-
%email_username% : the username part of the users email address associated with the Osirium PAM user = john.smith
-
%email_username_first_part% : the whole of the users first part of the email address associated with the Osirium PAM user = john
-
%email_username_first_initial% : the first character of the users first part of the email address associated with the Osirium PAM user = j
-
%email_username_last_part% : the whole of the users second part of the email address associated with the Osirium PAM user = smith
-
%email_username_last_initial% : the first character of the users second part of the email address associated with the Osirium PAM user = s
Note
Mappings are case insensitive and will be forced to lowercase when saved.
Account mapping patterns
| Case | 1 | 2 | 3 | 4 |
|---|---|---|---|---|
| Logon Name | john.smith_admin | joe.bloggs_admin | alice.cooper_admin | |
| sAMAccountName | john.smith_admin | joeb_admin | alicec_admin | administrator |
| FQDN | ad.companyX.net | ad.companyX.net | ||
| Explicit UPN | john.smith_admin@ad.companyX.net | joe.bloggs_admin@ad.companyX.net | alice.cooper_admin@companyX.com | |
| Implicit UPN (if no eUPN defined =logonname@fqdn) |
john.smith_admin@ad.companyX.net | joeb_admin@ad.companyX.net | alicec_admin@ad.companyX.com | administrator@ad.companyX.net |
| Resultant 'Account' column | john.smith_admin | joe_bloggs_admin | alice_cooper_admin@companyX.com | administrator |
| Standard User | john.smith | joe.bloggs | alice.cooper | |
| Mapping | %username%_admin | %username%_admin | %username%_admin@companyX.com | |
| Note | When FQDN = AD Auth Service FQDN | When FQDN = AD Auth Service FQDN | Builtin 'Administrator' does not have a logon name or display name |
-
On the Manage account mappings page, click the

NEW ACCOUNT MAPPINGbutton. -
In the New account mapping window, configure the pattern. The pattern will differ depending on whether you want to use the Domain FQDN or a UPN Suffix.
The following table gives you an example of how your pattern should be created:
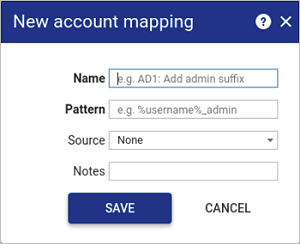
Fill in the following details:
Heading Description Name Internal name to identify the mapping and its purpose. Pattern Enter the pattern that will be applied to Osirium PAM user when accessing a device. NOTE Patterns are case-insensitive. Any capital letters typed in the Pattern field will save as lower-case.
Source Select the source that will be used to audit the account mapping entry. Notes Any additional information relating to the pattern. -
Click
SAVE. The pattern will now be available in the access level drop-down list when adding devices to a profile. See Manage Profiles.
Editing an account mapping
See Common Interface Functions section for inline editing.
Deleting an account mapping
Deleting a mapping will remove all devices using that mapping, from every profile which uses the mapping.
Matrix tab
The matrix lists all the mapping entries that have been created per user for all the account mapping patterns listed.
The account mapping matrix displays the full matrix of usernames created per user from the account mapping patterns. These results can be edited to allow for granular customisation of the mapping entry.
The information presented on the Matrix table includes:
| Heading | Description |
|---|---|
| Status icon | -  No account source to audit against. No account source to audit against.- - - |
| Username | Username of the user as listed in Osirium PAM. |
| Mapping Name | Name of the mapping the account entry is linked to. |
| Mapping | Mapping pattern that is applied to the username. |
| Entry | Username with the mapping applied. |
| Source | Source used to audit the entry. |
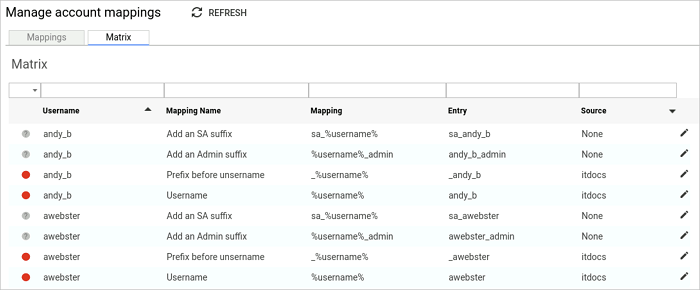
Only the mapping entry field can be edited.
When a mapping is deleted so are the matrix entries created from the mapping.
 Account name not found when audited against the account source.
Account name not found when audited against the account source. Account has been found but is not in a Known state.
Account has been found but is not in a Known state. Account verified by the account source and is usable.
Account verified by the account source and is usable.