Managing users
This section describes how Osirium PAM users are created and managed within the Admin Interface, covering the following:
- Manage users
- User creation checklist
- User authentication types
- Manage users page
- Creating users
- Bulk importing
- Cloning a user
- Editing a user
- Unprovision a user
- Named user page
Manage users
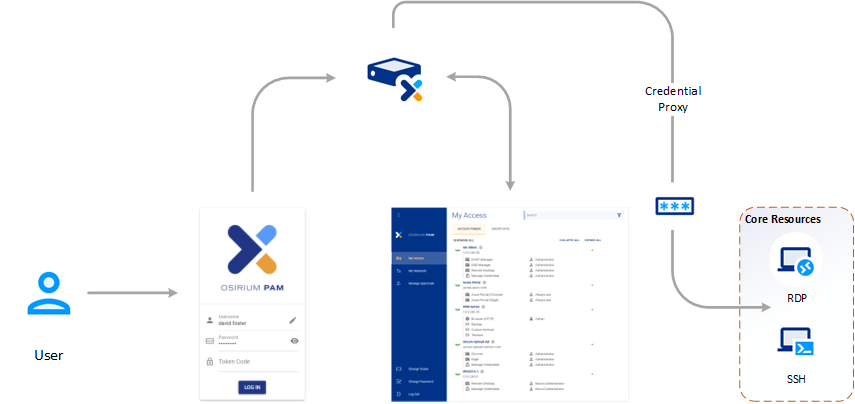
Osirium PAM user accounts are used to login to PAM from which they can gain access to:
- The Admin Interface.
- Device management tools.
Note
Privileges to devices are granted through Creating a new profile.
We strongly recommend using personal user accounts, not shared accounts, as these will allow you to easily monitor an individual's activity and review their privileged access.
User creation checklist
Before you start to create users consider the following:
User authentication types
Users can be created and authenticated in a number of ways so consider the following before starting.
-
Local authentication: the username and password are created by Osirium PAM and stored on the server. When configuring local authentication the following Auth type options are available:
-
External authentication: allows you to use an existing user (username/password). Once setup, Osirium PAM will consult with the external Account source to verify the user logon. When configuring external authentication the following Auth type options are available:
-
Multi-factor authentication: can be enabled to ensure a user is authenticated only after successfully providing a password and a token code. When users login, they will be presented with two fields: a Password field; and a Token code field. When configuring multi-factor authentication the following Auth type options are available:
-
Authentication delegation: allows the use of a third party identity provider (IdP) to authenticate user credentials. When configuring authentication delegation the following Auth type options are available:
Local
A local user is one whose username and password are created by Osirium PAM and stored on the server. When the local user logs on, the user will be checked against the list that exists in the database and its password verified.
To enhance security and implement a strong authentication policy for local user authentication, configure a password policy. See PAM Server Local Password Policy.
RADIUS
To enable users to be authenticated and authorised via your existing RADIUS server setup you will need to configure the following:
-
Add a RADIUS configuration that Osirium PAM can communicate with to verify and authenticate RADIUS users. See RADIUS Configuration.
-
Create the user account. The Username must match the username that already exists on the RADIUS Server and the correct authentication type must be selected. See Creating local users.
RADIUS Authentication process
When users login they will be presented with three fields, a Username field, a Password field, and a Token code field. Depending on your RADIUS Server authentication configuration, the user will enter a Username followed by either a Password or Token code or Password and Token code.
The following describes the possible authentication scenarios:
-
Password and Token code field sent individually: The user enters a Password and a Token code, firstly Osirium PAM will submit the Password to the RADIUS Server as a RADIUS: Access-Request. The RADIUS Server verifies the Username and Password and replies with a RADIUS: Access-Challenge which Osirium PAM then replies with the Token code in the subsequent RADIUS Access-Request. For this RADIUS Server configuration to work you will need to UNCHECK the Combine password and token code for RADIUS-only users settings. See Combined RADIUS which is checked by default.
-
Password and Token code field sent together: The user enters a Password and/or a Token code which will be joined together and sent as one to the RADIUS Access-Request for authentication. For this RADIUS Server configuration to work the Combine password and token code for RADIUS-only users setting must be CHECKED. See Combined RADIUS which is checked by default.
Active Directory
Before Active Directory can be used as your preferred user authentication type, you must ensure the following:
-
LDAPS must be enabled on the Active Directory. LDAPS will ensure that usernames/passwords and other information communicated between the PAM Server and the Active Directory will be kept confidential and secure.
-
An Active Directory must also be provisioned before users can be authenticated against it. See Adding an Active Directory.
-
Synchronise Active Directory users using User group synchronisation. See User Groups.
Local then RADIUS
The user will first have to enter a local user password followed by the RADIUS token. For configuration see RADIUS configuration.
Local then TOTP
The user will first have to enter a local user password as well as generate and enter a TOTP (Time-based One Time Password) to log on. For full details on how to setup a user to use an authentication type of Local then TOTP see here.
Active Directory then RADIUS
The user will first have to enter their Active Directory password followed by the RADIUS token. For configuration see Active Directory configuration and Manage Active Directories.
Active Directory then TOTP
The user will first have to enter their Active Directory password as well as generate and enter a TOTP (Time-based One Time Password) to log on. For full details on how to setup a user to use an authentication type of Active Directory then TOTP see here.
SAML2
Before authentication can be delegated to a third party identity provider (IdP), the SAML2 configuration is required to allow Osirium PAM to communicate with the Identity Provider (IdP). See SAML2 configuration.
Manage users page
The Manage users page allows you to manage user accounts. To view the Manage users page click Users in the left-hand menu. The Manage users page lists all the users and provides a high level overview of the accounts.
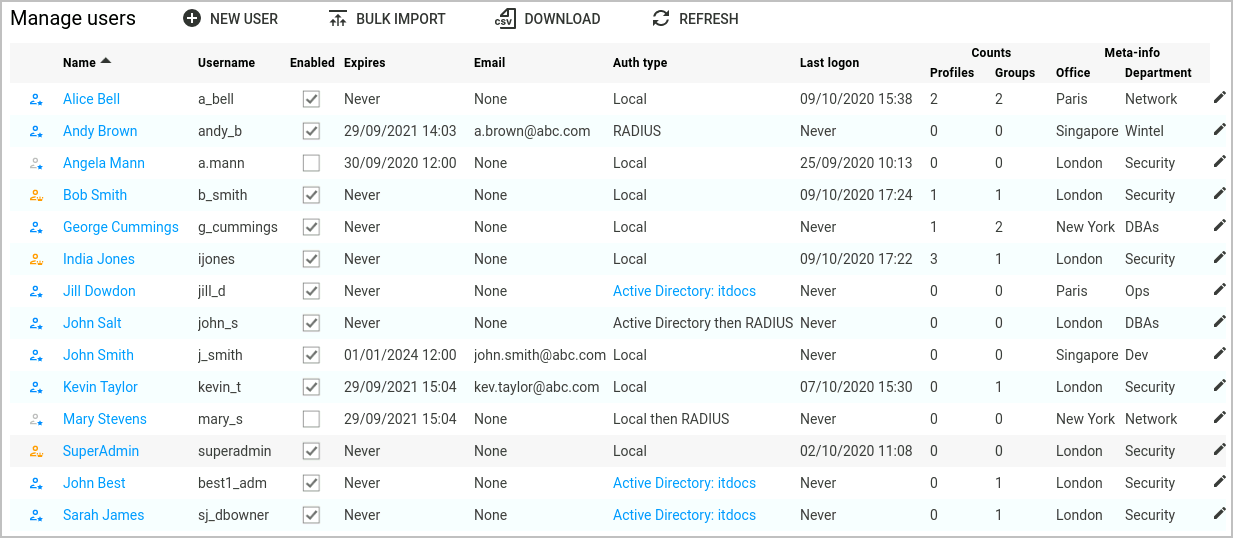
The following table describes the user states.
Note
The state of the user account will not be filtered to the external authentication if you are using one.
| Icon | Description |
|---|---|
 User/Auditor User/Auditor Owner/Admin Owner/Admin |
Enabled user account. All new user accounts will default to the Osirium PAM user role when created. This allows the user to logon to the UI. When a user is granted the Auditor role, the user will have limited access to the Admin Interface. When a user is granted the Owner or Admin role, the user icon will change from blue to gold. Members of the Owner role have full access to the Admin Interface. Members of the Admin role have full access with the exception of revealing credentials and generating a breakglass file. |
 User/Auditor User/Auditor  Owner/Admin Owner/Admin |
Disabled user account. A user is disabled when the user account expires. When an account is disabled, the user is unable to log onto the client to manage devices and run tasks. |
 Locked User Locked User  User/Auditor User/Auditor
|
The local account is locked if it exceeds the parameters set out in the PAM Server Local Password Policy. The user will be unlocked if: |
Creating users
Users can be:
- Created manually.
- Bulk imported through a csv template.
- Cloned from an existing user.
- Synchronised through Active Directory security groups.
To manually create a new user:
-
Click the

NEW USERbutton on the Manage users page.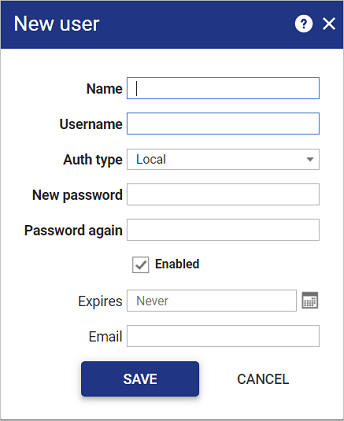
-
Fill in the following details to create a new user:
Field name Description Name: Display name and internal identifier. Username: Unique identifier used for logging in. Auth type Method that will be used to authenticate the user. New password: LOCAL AUTH TYPE ONLY
Create a login passwordPassword again: LOCAL AUTH TYPE ONLY
Re-enter the login password. Enabled
EnabledCheckbox ticked by default. Means user can login once created. Unchecking will create the user but prevent the user from logging in.
Expires OPTIONAL
Date on which the user will no longer be able to login.A blank field will default to never expire.
NOTE If using external authentication, this does not mean the account will be disabled on the account source. It will only disable the user's ability to log into Osirium PAM.
Email OPTIONAL
A valid email address is required to send notifications including Access Requests.Meta-info Select an entry if meta-columns have been configured. Note
Name/Username can’t have the same name as an existing user.
UTF-8 characters are supported in the name/username.
-
Click
SAVE.-
The Create Osirium PAM user task will be queued for creation.
-
Check the System queue page for progress.
-
Refresh the Manage users page to update the user status icon.
-
Bulk importing
If you have a number of users to create you can use the csv template and then import your user list. This is a more effective and quicker way of adding mutliple users to Osirium PAM.
Note
If you intend to use meta-columns then they should be added prior to downloading the bulk import CSV template. See Configure Meta-info.
To bulk import users:
-
On the Manage users page, click
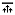
BULK IMPORT. -
Within the Import from CSV window, click
DOWNLOAD CSV TEMPLATE.If the PAM Server Browser (HTTP) tool is being session recorded, then you will need to use the Shared Drive mechanism for downloading files. For further details see Downloading a file using Shared Drive.
-
Open the users_[date].csv file. You will see an example given to follow the inputs required.
-
Add in your users to be imported. See User authentication types for requirements depending on the authentication type you will be using.
Field name Description Name: Display name and internal identifier. Username: Unique identifier used for logging in. Enabled Enter True to enable the user account once created, allowing the user to logon to Osirium PAM or False to disable the user account. Expires OPTIONAL
Date on which the user will no longer be able to login.A blank field will default to never expire.
NOTE If using external authentication, this does not mean the account will be disabled on the account source. It will only disable the user's ability to log into Osirium PAM.
Email OPTIONAL
A valid email address is required to send notifications including Access Requests.Auth type Method that will be used to authenticate the user. Password: LOCAL AUTH TYPE ONLY
Enter the login password to be set.Meta-info Add the meta data to be set if configured. Note
Name/Username can’t have the same name as an existing user.
UTF-8 characters are supported in the name/username.
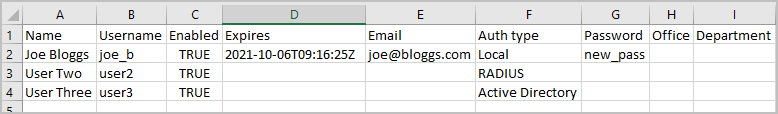
For example:
-
Now within the Import from CSV window, click
Choose File.If the PAM Server Browser (HTTP) tool is being session recorded, then you will need to use the Shared Drive mechanism for uploading files. For further details see Uploading a file using Shared Drive.
-
Select the uploaded users bulk import file and click
OPEN. -
Click
IMPORT. -
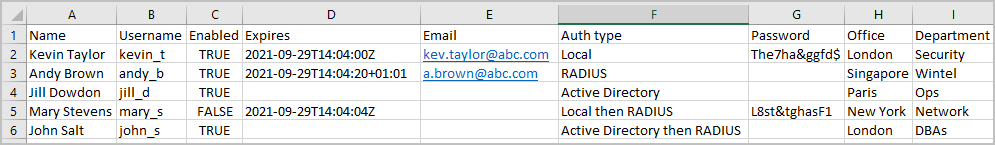
The entries in the CSV file are added and displayed in the Bulk import users window.
-
Before you click
IMPORTnote the following.-
To import all the users listed, click the

SELECT ALLbutton. -
To import only a selection of users from the list, hold the CTRL key and select the users you want to import from your bulk import list.
-
Errors will be highlighted with a warning icon.
-
If warnings are not fixed then you will get an error when you click
IMPORT.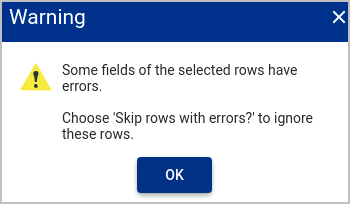
-
You can select the Skip rows with errors to ignore the rows with errors and import all the others.
-
You can update any user settings by clicking on the
 at the end of each row.
at the end of each row. -
If there are no errors highlighted then all users will be imported in the list.
-
To set the password for all the users listed, click the

SELECT ALLbutton and then click theAPPLY PASSbutton. -
To set the password for only a selection of users from the list , hold the CTRL key and select all the users you want to set the passwords for and then click the
APPLY PASSbutton. -
To disable a user when created, click
 at the end of the row and deselect the
at the end of the row and deselect the Enabledcheckbox.
-
-
Click
IMPORT. -
Within the Question window, click
YESif you are happy to proceed with the bulk import. -
Within the Action queue window, users will be imported and queued for creation. If you have a lot of users in your bulk import then you can choose to
Continue in the backgroundor if the imports have been completed, clickDONE.The Manage users page will automatically be updated.
Cloning a user
Cloning an existing user allows you to:
-
Create a new user who inherits the same user account settings.
-
Adds the new user to all the same profiles as the user being cloned.
-
Provides access to the same tasks and devices with the same access levels.
To clone a user:
-
Right-click the user on the Manage users table that you want to clone.
-
Select
Clone. -
Within the Cloning [user name] window, you will be prompted to enter the details for the new user to be created.
-
Fill in the following details to create a new user:
Field name Description Name: Display name and internal identifier. Username: Unique identifier used for logging in. Auth type Leave as per cloned user. New password: LOCAL AUTH TYPE ONLY
Create a login passwordPassword again: LOCAL AUTH TYPE ONLY
Re-enter the login password. Enabled
EnabledLeave as per cloned user. Expires Leave as per cloned user. Email OPTIONAL
A valid email address is required to send notifications including Access Requests.Meta-info Leave as per cloned user. Note
Name/Username can’t have the same name as an existing user.
UTF-8 characters are supported in the name/username.
-
Click
PROCEED. -
Within the Question window, click
YESto proceed with creating the user.-
The Clone user task will be run.
-
The Profiles user update task will be run to add the user to the same profiles as the cloned user.
-
The cloned user will appears on the Manage users page.
Note
If necessary, click the
Refreshbutton to manually update the Manage users page. -
Editing a user
See the Common Interface Functions section for inline editing.
Unprovision a user
Unprovisioning a user deletes the user's account from Osirium PAM and deletes any personalised user accounts created by Osirium PAM on any devices they have permission to access.
Once deleted, the user cannot be reinstated. The user would have to be recreated as a new user and reconfigured.
Note
If this is an Active Directory user account which still belongs to an Active Directory user group, then the unprovisioned account will be recreated in Osirium PAM when an audit is triggered.
To unprovision a user:
-
On the Manage users page, right click on a user and then click

Unprovision. -
Within the Question window, click
YESif you are sure you want to unprovision the user. -
During the unprovisioning:
-
The user will no longer be able to logon to the UI and single sign-onto devices.
-
If the user is logged onto the UI, they will be logged out and any open device sessions disconnected. Any further attempts to login will fail.
-
The user account will be removed from all profiles.
-
The user's personalised accounts on any devices will be deleted.
-
The user will be removed from all user groups.
-
The user account will be deleted from Osirium PAM.
To unprovision multiple users, highlight a number of users, then right-click and click

Unprovision. ClickYES. -
Named user page
This page provides details of an individual user and a summary of their access and can be accessed by clicking on the users name listed on the Manage users page. Use this page to review and manage a users details and update access requirements.
Available on this page:
-
Users details: clicking on
 will allow you to update all the users details except the Username field.
will allow you to update all the users details except the Username field. -
Profiles: lists the profiles the user belongs to which gives them access to devices. Does not include profiles that the user belongs to through user groups. To add/remove profiles click on
MANAGE. -
User groups: lists the user groups the user belongs to. Click the link to view the user group and which profiles it has been added to. To add/remove user groups click on
MANAGE. -
Device access: provides a list of all the devices a user has been granted access to and the permission level assigned. The information presented includes the following:
Header Description 
Click the arrow to reveal more information. Device Name of the devices access has been granted to. Via States if access has been granted through a profile or through a user group which has been added to a profile. Access roles List the access level the user will have when connecting to the device. Available access levels may include:
Configured within a template:
- Role: the available device access levels Osirium PAM uses when creating personalised accounts on the device.
- Account: Managed and Known accounts that exist on the device are used to single sign-on to the device.
Configured within the Admin Interface:
- Mapping: a predefined account mapping is used to map the users username to an existing account on the device or account source (local accounts, Active Directory, Static vault).
- Always ask: User will be prompted for a username/password when connecting to the device.
- Pass-through: The username/password used to login into Osirium PAM is used to single sign-on to the device.Accounts If an account is listed, this is the account that Osirium PAM will use to single sign-on the user to the device. Mappings If the name of an account mapping is listed then the users username will be mapped to an existing account on the device using a mapped account created in the account mapping matrix. Recorded If checked, the user session on that device will be recorded. Last Connection Date and time the device was last accessed by the user.
Note
User role based access to the Admin Interface is default for all users created and can’t be removed or be seen within a profile.

 Owner/Admin
Owner/Admin