System configuration
The System configuration page provides information relating to Osirium PAM and allows you to configure a number of different settings.
The following tabs are available:
- Licencing tab
- Certificates tab
- Fingerprints tab
- High Availability tab
- SAML2 tab
- System settings tab
- Client settings tab
- Connection settings tab
- Network Settings tab
Licencing tab
The licencing page provides an overview of the licence you have bought and the features that have been activated as part of your licence.
It can help you manage your allowance limits against your current configurations and when you are in need of an upgrade to your licence limits.
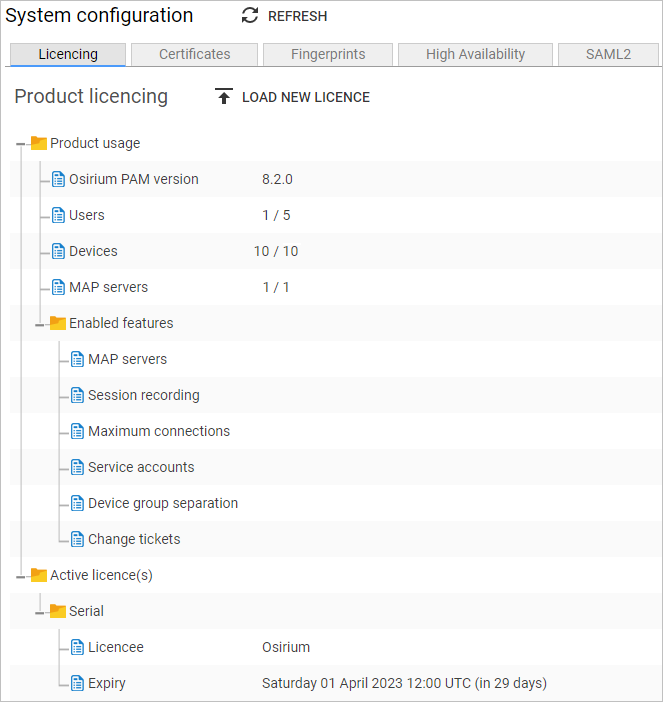
The following information is presented on the page:
| Heading | Description |
|---|---|
| Product usage | Osirium PAM version: The version that has been installed and is currently running. Users: Displays the total number of created user accounts against the total number of allowed user accounts. The support account and the SuperAdmin account will not be included in this count. Devices: Displays the total number of provisioned devices managed by against the total number of allowed devices. The PAM Server device will not be included in this count. MAP servers: Displays the total number of provisioned MAP Servers used with Osirium PAM against the total number of allowed MAP Servers. |
| Enabled features | Features available under this licence are displayed here, which may include: MAP servers Session recording Service accounts Change tickets Device group separation |
| Active licence(s) | Licencee: Name of the organisation or individual which the licencing has been assigned to. Expiry: The date/time the license is due to expire and the number of days remaining. |
Licence limits
When a licence total for Users, Devices or MAP Servers has been reached, if you attempt to add more, a message will be displayed stating that the licence limit has been met.
Licence expiration
When a licence is within 30 days of expiry a countdown warning message will appear in the banner on the Admin Interface.
A licence will expire at midday UTC of the expiry date. Once expired:
- The only access available to Osirium PAM will be to the product licencing upload page on the Admin Interface.
- Only the PAM Server will be displayed in the Device list. All other devices will be hidden.
If a new licence is uploaded before the current licence has expired, the existing licence will be superceded by the new licence.
Uploading a license
To load a licencing:
-
Click the
LOAD NEW LICENCEbutton. A Question window opens. -
Click
YESto proceed. -
Within the Upload licence window, click
Choose File.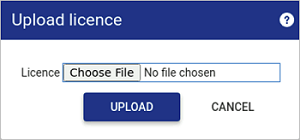
-
Within the File upload page navigate to and select a valid Osirium PAM licence file.
If the PAM Server Browser (HTTP) tool is being session recorded, then you will need to use the Shared Drive mechanism for uploading files. For further details see Uploading a file using Shared Drive.
-
Within the Upload licence window, click
UPLOAD. The new licencing file will be loaded. The licencing information is updated to reflect any changes.
Certificates tab
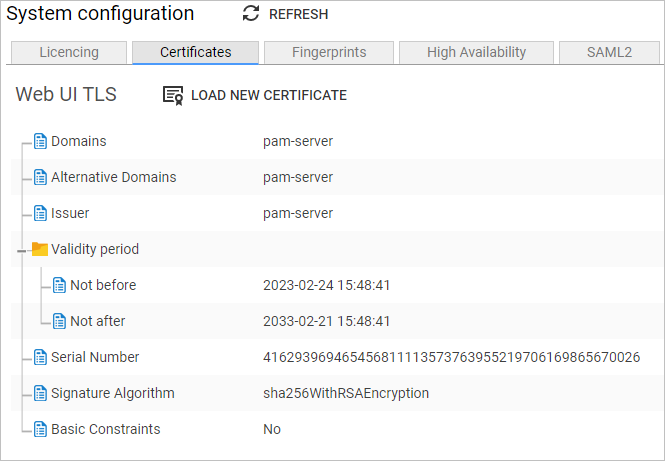
By default, Osirium PAM provides a generic certificate to allow secure web connections to the PAM UI and Admin Interface. On this page you will see information about the current certificate that is being used.
Certificates are used to protect the data being sent between Osirium PAM by encrypting the data before it is sent and then decrypting the data when it reaches its destination.
The certificate types supported by Osirium PAM are:
- Trusted Certificate (.crt/.pem) with an accompanying RSA Private key (.key). Both are required for a successful upload.
- Single PKCS #12 archive file (.pfx) which contains both the certificate and key. These are commonly used in Microsoft environments.
We recommend that you upload a trusted certificate valid within your organisation. For further details on the types of signed certificates that can be used in Osirium PAM click here.
Upload a certificate
The steps to upload a certificate differ depending upon the certificate type.
Upload a certificate with RSA private key
To upload a trusted certificate with RSA private key:
-
On the Certificates tab, click
LOAD NEW CERTIFICATE. -
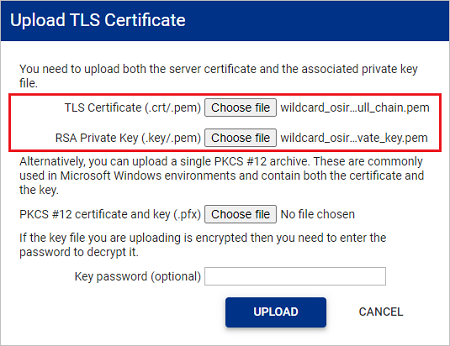
In the Upload TLS Certificate window, upload your trusted certificate and RSA private key. Both are required for a successful upload.
If the PAM Server Browser (HTTP) tool is being session recorded, then you will need to use the Shared Drive mechanism for uploading files. For further details see Uploading a file using Shared Drive.
TLS Certificate: Uploaded certificates will be verified to ensure they are an X.509 certificate with a .crt/.pem file format.
RSA Private Key: Uploaded keys are verified to ensure they are an rsa key with a .key/.pem file format.
-
If the private key you are uploading has been encrypted, enter the password in the Key password (optional) input box.
-
Click
UPLOAD. The certificate is uploaded.
Upload a PKCS12 file
To upload a PKCS #12 archive file:
-
On the Certificates tab, click
LOAD NEW CERTIFICATE. -
In the Upload TLS Certificate window, upload your PKCS #12 file.
If the PAM Server Browser (HTTP) tool is being session recorded, then you will need to use the Shared Drive mechanism for uploading files. For further details see Uploading a file using Shared Drive.
The certificate contained within the PKCS #12 file will be verified to ensure it is a X.509 certificate.
The private key contained within the PKCS #12 file will be verified to ensure it is an rsa key.
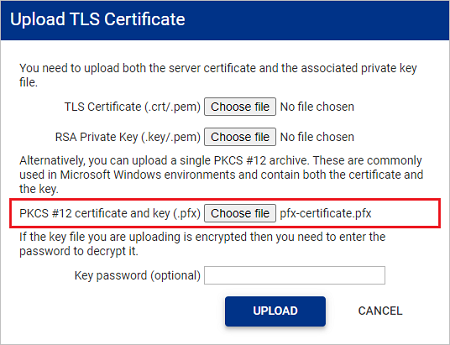
-
If the private key you are uploading has been encrypted, enter the password in the Key password (optional) input box.
-
Click
UPLOAD. The certificate is uploaded.
Fingerprints tab
Fingerprints help guard against man-in-the-middle attacks on devices, in which attackers can secretly redirect network traffic between Osirium PAM and the device to monitor and manipulate the flow of information.
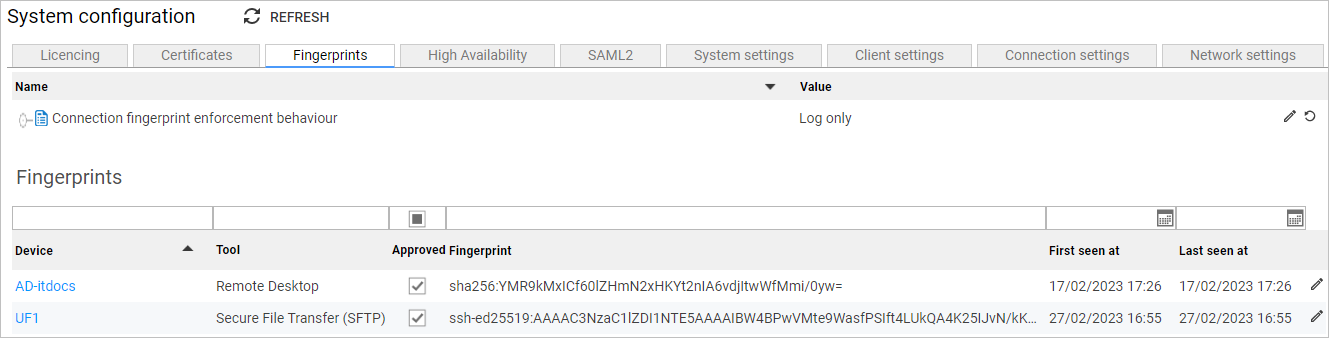
When a device is deployed on Osirium PAM, a fingerprint is generated which Osirium PAM associates with the device. When connecting, Osirium PAM checks that the fingerprint of the device matches the fingerprint Osirium PAM associated with that device. By default, if the device fingerprint is not approved, Osirium PAM notes the discrepancy in the Logs page, but does not block the connection.
Connection fingerprint enforcement behaviour
If you want Osirium PAM to block connections to devices with unapproved fingerprints, you can configure the Connection fingerprint enforcement behaviour.
To configure the Connection fingerprint enforcement behaviour:
-
On the table, click the
 icon for Connection fingerprint enforcement behaviour. The Edit entry window
appears.
icon for Connection fingerprint enforcement behaviour. The Edit entry window
appears.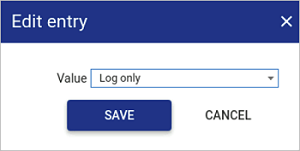
-
From the Value drop-down, select one of the following options.
Value Details Log only - Osirium PAM allows connections to devices with unapproved fingerprints.
- Connection details are logged in the Logs page on the Key Verifier tab.Block - Osirium PAM blocks connections to devices with unapproved fingerprints.
- Users attempting the connection receive an error message.
- Connection details are logged in the Logs page on the Key Verifier tab. -
Click
SAVE. The Connection fingerprint enforcement behaviour value is applied.
Fingerprints table
The Fingerprints table allows you to select fingerprints to associate with designated devices. The following details are available:
| Column | Details |
|---|---|
| Device | Provisioned device on your PAM Server. |
| Tool | Tool the fingerprint is attached to. |
| Approved | If selected  , the fingerprint is associated with the corresponding device. , the fingerprint is associated with the corresponding device.If deselected  the fingerprint is not associated with the corresponding device. the fingerprint is not associated with the corresponding device.You can configure the PAM Server to block connections to devices with unapproved fingerprints using the Connection fingerprint enforcement behaviour above. |
| Fingerprint | The fingerprint generated for the device. The PAM Server generates fingerprints from the device SSH key or certificate. |
| First seen at | The first time the PAM Server connected to, or ran a task on, the device. |
| Last seen at | The last time the PAM Server connected to, or ran a task on, the device. |
High Availability tab
The High Availability page provides an overview of the servers that have been configured for High Availability (HA). For further details see HA Guide.
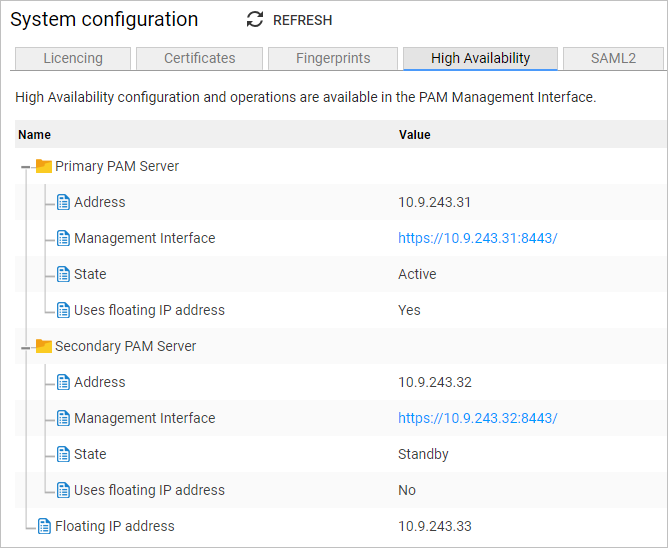
The following details are available:
| Column | Details |
|---|---|
| Primary PAM Server | In BAU, the Primary is the active PAM Server through which all user traffic flows. The actual role the server is performing will be dependant upon its current State. |
| Secondary PAM Server | In BAU, the Secondary is the standby PAM Server that is continually maintaining a replica of Primary’s database. The actual role the server is performing will be dependant upon its current State. |
| Floating IP address | The IP address assigned to the floating IP (if configured). |
| Address | The IP address assigned to the PAM Server. |
| Management Interface address | The URL to connect to the web-based interface which is used to manage and configure HA. Users authenticate using their PAM user credentials and is only available to members of the Owner role. |
| State | Active The server is operational and receiving all user traffic. Standby Demoted Failed |
| Uses floating IP address | When a floating IP address has been configured, 'Yes' will be displayed for the server it is currently directed to. |
Note
If HA has not been configured, all values will be displayed as Not configured.
SAML2 tab
You can configure Osirium PAM to use a third-party identity provider (IdP) using Security Assertion Markup Language v2.0 (SAML2) to authenticate user logon credentials.
Setting up this configuration will enable Osirium PAM, the service provider, to delegate authentication to an external third party, the identity provider (IdP).
When a user logs on, Osirium PAM will request authentication from the identity provider. The identity provider is then responsible for authenticating the user credentials and notifying Osirium PAM. If the authentication has been successful, Osirium PAM will authorise the user and permit access.
The service provider configuration is used to construct the SAML2 metadata which will allow the Osirium PAM service to communicate and interact with the IdP.
Configuring SAML2
To configure:
-
Click on the
 next to Service provider configuration.
next to Service provider configuration. -
Witin the Edit entry window enter the details as follows
Note
The details entered will depend upon the Identity Provider that you will be delegating authentication to. Click here for instructions for configuring Osirium PAM SAML2 Authentication with Azure.
Also click here for details on the limitations and troubleshooting when using Microsoft Azure.
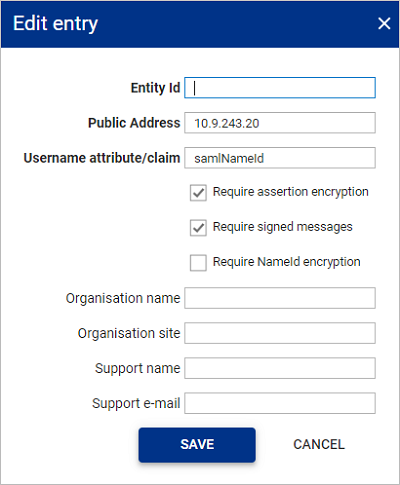
Heading Description Entity Id Enter a name or url to identify the service provider. This id will be used when configuring the IdP. Public Address The Public Address is the FQDN or IP address where the SAML Assertion is HTTP POSTed by the users browser. This could be the PAM Server or a PAM UI instance but it must be accessible by the user’s browser. Default value is set to the IP address of the PAM Server or HA floating IP address if configured.
Username attribute/claim Default is samlNameId. This name needs to match the name of the attribute/claim once configured on your IdP. This is required for Osirium PAM to authorise the user once the IdP has authenticated the user. The username extracted from the SAML Assertion will be used to match an existing local user with the same username within Osiruim PAM user list.
NOTE: As Osirium PAM does not permit the ‘@’ character in usernames if the value is an e-mail address the portion before the ‘@’ is extracted and used.
Require assertion encryption Requires the Identity Provider to encrypt the whole SAML Assertion. Require signed messages Requires the Identity Provider to sign SAML messages. Require NameId encryption Requires the Identity Provider to encrypt the NameId element of the SAML Assertion. Organisation name Enter your organisation details that will be used by the IdP to identify you. Organisation site Enter your organisation details that will be used by the IdP to identify you. Support Name Enter the name of the support person/group that will manage IdP related issues. Support e-mail E-mail address of the support person/group that will manage IdP related issues. -
Click
SAVE. -
Click
DOWNLOAD SERVICE METADATA. This file is required by the IdP to construct the SAML2 metadata.If the PAM Server Browser (HTTP) tool is being session recorded, then you will need to use the Shared Drive mechanism for downloading files. For further details see Downloading a file using Shared Drive.
-
Once you have configured your IdP, you will need to upload the signing certificate to complete the configuration in Osirium PAM. This will then allow the Osirium PAM service to communicate and interact with the IdP to authenticate users with an Auth type set to SAML2.
If the PAM Server Browser (HTTP) tool is being session recorded, then you will need to use the Shared Drive mechanism for uploading files. For further details see Uploading a file using Shared Drive.
For instructions on configuring Osirium PAM SAML2 Authentication within Microsoft Azure click here.
Download Service Metadata
Click the DOWNLOAD SERVICE METADATA button to download the Osirium PAM service SAML metadata file that will be required when configuring the IdP.
If the PAM Server Browser (HTTP) tool is being session recorded, then you will need to use the Shared Drive mechanism for downloading files. For further details see Downloading a file using Shared Drive.
Upload Identity Provider Metadata
Click the UPLOAD IDP METADATA to upload the IdP metadata file that will be required by Osirium PAM to communicate and interact with the IdP.
If the PAM Server Browser (HTTP) tool is being session recorded, then you will need to use the Shared Drive mechanism for uploading files. For further details see Uploading a file using Shared Drive.
System settings tab
The following can be configured on the System settings tab:
- File store status
- Support account
- PAM Server local password policy
- Active Directory password generation complexity
- Enable pass-through
- Debug task logging
- Debug API logging
- Debug UI logging
- File store
- SMB share configuration
- Scheduled session archive
- Scheduled file removal
- User group synchronisation interval
- Active Directory user group sync new user authentication type
- Backup schedule
- Backup breakglass passphrase
File store status
When a file store has been configured, the File Store Status button displays details of the configured file store. These details can assist when troubleshooting file store connectivity issues.
-
Click on the
FILE STORE STATUSbutton.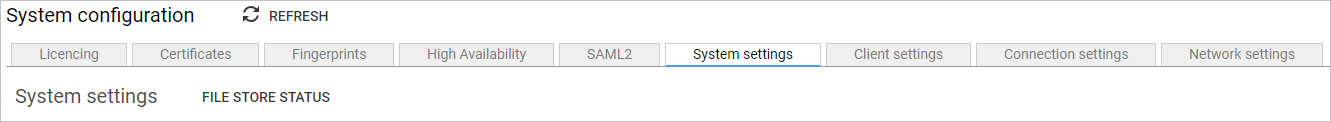
-
The following details are displayed:
Field name Description File store The configured file store option and its capacity. UNC path The UNC path of the configured file store option. Username The username used for the configured file store option. Reported issues Details of any reported issues. -
To refresh the File store status details click
REFRESH. -
Click
OK.
Support account
The support account (osirium_support) is a PAM Server Ubuntu server administrative account. It is created during the installation of the PAM Server. This account is useful if you are unable to access the Admin Interface and want to troubleshoot issues through the command line.
The default setting is disabled and no password set.
Note
It should always be enabled and a password set when upgrading or carrying out a system restore.
To enable:
-
Click on the
 next to Support account (User name: osirium_support).
next to Support account (User name: osirium_support). -
Check the Enabled box and type in a password.
-
Click
SAVE.
PAM Server local password policy
If you are creating users that will be authenticated by Osirium PAM this setting will allow you to create and set a password policy to implement a greater complexity and stronger authentication on the passwords set for user accounts. Only passwords that meet the password policy will be allowed ensuring all passwords met the required criteria.
Note
This will not apply to externally authenticated Active Directory or RADIUS users.
To configure:
-
To the right of PAM Server local password policy, click the
 icon.
icon.
-
Set the appropriate policy using the fields described below.
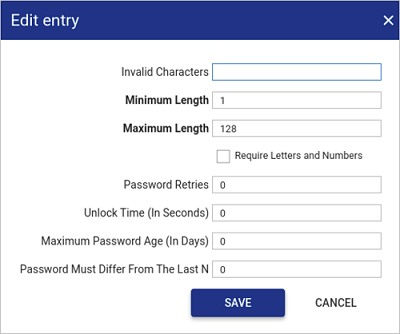
Field name Description Invalid Characters Enter any characters you don't want used in a password.
Any password containing these characters will be disallowed.Minimum Length The password must be equal to or greater than the minimum length set. Maximum Length The password must be less than or equal to the maximum length set. Require Letters and Numbers If true (tickbox checked), the password must contain both letters and numbers. Password Retries The user will be locked if an incorrect password is entered this many times.
If set to 0, the user will be allowed infinite retries to enter their password.Unlock time
(In Seconds)Time the user will have to wait before the account is automatically unlocked. Maximum Password Age
(In Days)From the moment a password is changed, it starts aging. When the maximum age is exceeded, the user will be forced to change their password at next logon. If set to 0, the password will not expire.
Password Must Differ From The Last N When the user sets a new password, it must be different from the last N passwords they have used. If left as the default 0, the password does not have to differ from any passwords used before.
-
Click
SAVE.
Active Directory password generation complexity
The password complexity of an Active Directory account managed by Osirium PAM can be set here. You can set the length of the password as well as any special characters that can used within the password.
To update the complexity settings:
-
Click on the
 icon.
icon. -
Set the password length and special characters that should be used when setting a password for an Active Directory managed account.
-
Click
SAVE.
Enable pass-through
The pass-through feature allows users to single sign-on to devices using personalised accounts that preexist on the device. When a user logs onto the UI their credentials (username/password) are cached and encrypted to an instance on the PAM Server.
Then, when the user connects to a device which has been configured to use an access level of pass-through (see Creating a New Profile), the cached credentials are used to single sign-on to the device.
Note
Only the following authentication types can be used with pass-through:
- Active Directory: The password is cached.
- Active Directory then RADIUS: only the password is cached (not token).
- Active Directory then TOTP: only the password is cached (not token).
Cached pass-through credentials are saved as case sensitive. To ensure successful pass-through the username/password must match the users pre-existing device account (username/password).
When a user logs out or disconnects from the UI, their credentials are removed from the cache. Also, if the PAM Server is restarted (specifically the userauth service) all cached pass-through credentials are removed.
The pass-through feature is Enabled as default which means all user credentials will be cached when logged onto PAM.
If this feature is Disabled at anytime, profiles that have devices with pass-through access levels will show as greyed out in the UI for all user in the profile.
To change the setting:
-
Click on the
 icon.
icon. -
Check or uncheck the
Enabledbox as per the setting required. -
Click
SAVE.
Debug task logging
If you want more detailed debug messages from your PAM Server you can turn on the debug logging level. It can be helpful and provide more clues if you come across issues.
When enabled, the debug logging messages will be available on the System configuration > Logs page on the Admin Interface.
To enable:
-
Click on the
 icon.
icon. -
Check the
Enabledbox. -
Click
SAVE.
Debug API logging
If you require more detailed messaging and logging of the API function then you can turn on the debug level for the API. It can be helpful and provide more clues if you come across issues.
To enable:
-
Click on the
 icon.
icon. -
Check the
Enabledbox. -
Click
SAVE.
Debug UI logging
If you require more detailed messaging and logging of the UI you can turn on the debug level for the UI. It can be helpful and provide more clues if you come across issues.
To enable:
-
Click on the
 icon.
icon. -
Check the
Enabledbox. -
Click
SAVE.
File store
We recommend that you configure a file store to avoid disk space issues and to hold some of the larger files. This will ensure that the internal PAM Server system disk does not fill up too quickly allowing for a smoother running of system services and tasks.
Configuring and attaching a file store will allow your PAM Server to save the following files directly onto the selected file store:
- Backups.
- Techouts.
- Session recordings.
- Session archives if configured.
Warning
If you are using PAM HA it is strongly recommended that an SMB share is configured. Without an SMB share you will not be able to failover without loss of data.
To configure, you will firstly need to configure the SMB share configuration and then configure the File store to use the SMB share.
Note
If you already have a file store configured, and you are changing to a different file store option, you can move all files to the newly configured file store using the CONSOLIDATE button on the Manage files page.
To add a file store:
-
Firstly, you will need to add a virtual hard drive to your PAM Server or create an SMB share which should be done in accordance with your company policy.
-
Click on the
 icon.
icon. -
Choose an appropriate option from the drop-down box.
Field name Description Data disk An external data disk that will be mounted by the PAM Server. SMB share An SMB share used for HA.
NOTE SMB share configuration settings must also be set.System disk The internal system disk of the PAM Server.
Not Recommended -
Click
SAVE.If SMB share is selected you must also configure the SMB share configuration settings in order to use the SMB share.
If Data disk is selected, Osirium PAM will partition, format and map to the external drive.
Once successfully mapped and configured, the disk usage bar on the Manage files page will be updated and display both the system disk and selected file store.
From here you can monitor your disk status to manage your storage levels and take precautions if your disk space is getting full.
Note
The selected file store may take a little time to appear on Admin Interface, depending on the size of the disk that is being configured.
SMB share configuration
Configuring an SMB share file store will allow your PAM Server to save the following files directly onto the selected file store:
- Backups.
- Techouts.
- Session recordings.
- Session archives if configured.
The SMB share is also used for HA to enable a Primary PAM Server to failover to the Secondary PAM Server without loss of data.
| Field name | Description |
|---|---|
| UNC path | The UNC path by which PAM can connect to the SMB share. For example \\server-name\shared-resource-pathname |
| Username | The username of the SMB share location. |
| Password | The password of the SMB share location. |
| Options (comma-separated) | Optional Allows additional parameters to be passed to the SMB share as a comma separated list if required. |
Note
After configuring the SMB share, navigate to the System queue and confirm the Device sync parameters setup task was successful.
Scheduled session archive
If you are session recording all your users on a daily basis then you will be creating a lot of recorded files on your system. This setting will allow you to manage the recordings being saved and help you with archiving the older session recordings for storage and backup.
Implementing a scheduled archive of session recordings will also allow you to manage disk space on your system or file store. The schedule is based on the age of the recording and will automatically be archived when they reach the age limit set.
When a scheduled session archive setting has been configured it will:
-
Run the Archive Session task everyday at midnight and archive any UI sessions that are older than the age (days) set.
When a session has been archived it will be marked as archived on the Device access report page on the PAM UI sessions section.
-
Store the archived file in the file store. Will default to the system disk, or if configured data disk or SMB share.
-
List the archived session file on the Manage files page from where it can be downloaded.
-
Copy the archived file to a remote backup server if one has been configured. See Remote Backup Server Configuration.
-
Delete the session recordings and database once successfully archived.
Note
For new installations of PAM, the Scheduled session archive setting will automatically be set to 90 days. If required this value can be changed to meet your organisations retention policy.
However if the value is set to 0, the 90 days retention value will automatically be re-applied when the PAM Server is next upgraded.
To configure:
-
Click on the
 icon.
icon.
-
Check the
Enabledbox.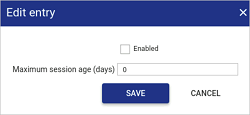
-
In the Maximum session age (days) field, type in the number of days before a session is to be archived.
-
Click
SAVE.
Scheduled file removal
The number of device files created can grow rapidly so to help easily manage older files you should configure a schedule that will automatically delete files when they reach a certain age. This will also help you manage your disk space, ensuring stored files don't fill up your disk space which could slow your system down.
The deletion of files will be based on their age. But before you enable this schedule make sure you have any backup requirements in place, especially if you need to backup the files before they are deleted.
Note
For new installations of PAM, the Scheduled file removal setting will automatically be set to 90 days. If required this value can be changed to meet your organisations retention policy.
However if the value is set to 0, the 90 days retention value will automatically be re-applied when the PAM Server is next upgraded.
To configure:
-
Click on the
 icon.
icon.
-
Check the
Enabledbox.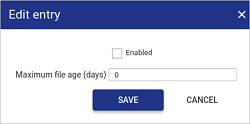
-
In the Maximum file age (days) field, type in the number of days before a file is deleted.
-
Click
SAVE.
The File removal task is run everyday at midnight and will now remove any files that are older than the age (days) set.
User group synchronisation interval
This setting should be used to create an automated synchronisation between the user groups in Osirium PAM linked to user groups on your Active Directory. This will help ensure that the Active Directory users within the group are kept up to date and any changes (removed/added users, password changes etc) are reflected in Osirium PAM.
Define in minutes how often you want Osirium PAM to synchronise user groups with your Active Directory.
To configure:
-
Click on the
 icon.
icon. -
The default value is set to 15 minutes. The value must be greater than or equal to 5.
-
Click
SAVE. The User Group Synchronisation task will be run against each Active Directory user group listed on the Manage user groups page and make any necessary updates.
Active Directory user group sync new user authentication type
This setting should be used to automate the authentication type setting of all new users that are synchronised through an Active Directory user group. See Managing user groups.
To select the authentication type setting that will be applied to new users that are synchronised through an Active Directory group:
-
Click on the
 icon.
icon. -
The external authentication type values that can be set for the synchronised Active Directory user are:
- RADIUS: this authentication type setting means that the user will use their RADIUS username to logon. The user doesn't need to enter a password as the existing RADIUS user password will be used to authenticate them into Osirium PAM.
- SAML2: this authentication type setting means that the user will use their Active Directory username/password to logon . Osirium PAM will then request authentication from the identity provider. The identity provider is then responsible for authenticating the user credentials and notifying Osirium PAM. If the authentication has been successful, Osirium PAM will authorise the user and permit access.
- Active Directory: this authentication type setting means that the user will use their Active Directory username/password to log on. Osirium PAM will consult with the Active Directory to verify the user logon before logging the user on.
- Active Directory then TOTP: this authentication type requires a multi-factor login meaning a user will have to enter their Active Directory username/password as well as generate and enter a TOTP (Time-based One Time Password) to log on.
- Active Directory then RADIUS: this authentication type requires a multi-factor login meaning a user will have to enter their Active Directory username/password as well as a RADIUS token to log on.
-
Click
SAVE.
Backup schedule
This setting allows you to configure scheduled backups of the PAM Server.
To configure scheduled backups:
-
Click on the
 icon. The Edit entry window opens.
icon. The Edit entry window opens. -
In the Value field, select an option. You add additional options by creating a new schedule. See Manage Schedules for details.
-
Click
SAVE. The backup schedule is applied.
Backup breakglass passphrase
This setting allows you to configure a passphrase to protect the KeePass file containing your device credentials. A passphrase must be configured in order for the KeePass file to be stored in the archived backup file that is created when you run a backup task on Osirium PAM.
To set a backup breakglass passphrase:
-
Click on the
 icon. The Edit entry window opens.
icon. The Edit entry window opens. -
In the Passphrase field, type a passphrase.
-
Click
SAVE. The backup breakglass passphrase is applied.
Client settings tab
The following can be configured on the Client settings tab:
Client colour
The colour option allows you to specify a colour for the UI. This is useful when you want to distinguish the connections made to different Osirium PAM.
To change the colour:
-
Click on the
 icon.
icon. -
Enter a HEX colour code; or
Click the icon to use the Select a Color window:
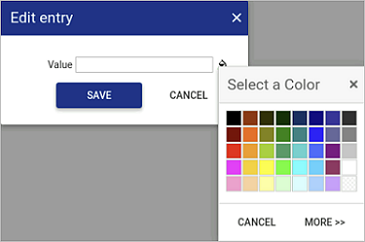
-
Click
SAVE. Now when a user logs onto the UI, the browser tab icon will contain the colour configured.
Connection settings tab
The following can be configured on the Connection settings tab:
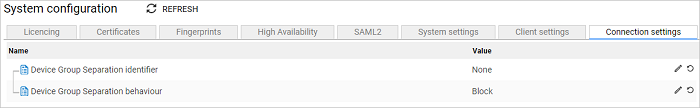
Device group separation identifier
Device group separation allows you to restrict access to device tools from multiple customers, to ensure that workstations don’t become a bridge point for data.
Before creating a group separation identifier, you need to create a meta-column entry of type Device. See Configure meta-info.
The meta-column values define the groups that are available. When a user connects to device tools through the UI, the group separation identifier controls which sets of device tools they can use at the same time.
To configure the group separation identifier:
-
Click on the
 icon.
icon. -
Choose the appropriate option from the drop-down box.
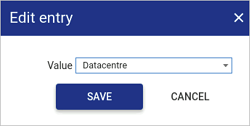
-
Click
SAVE. Now the values in the device type meta-column will determine which device tools can be accessed after the first device tool connection has been made.
For example:Device Meta-column value Device A Group 1 Device B Group 1 Device C Group 2 Device D Group 2 From the UI, if a user opens a tool from Device A which belongs to Group 1, the tool opens successfully. Then, whilst Device A is open, if the user opens a tool from Device B, then this will be allowed.
In the default block mode, if the user has a device tool from Group 1 open and then tries to open a tool on Device C which belongs to Group 2, then the user will be unable to access the tool and an error message will be shown:
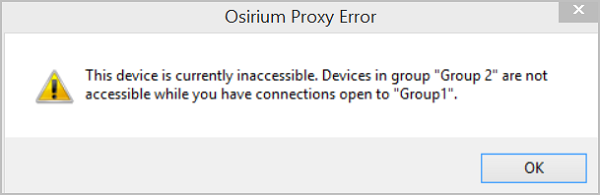
Only when all Group 1 connections have been closed can the user open device connections from Group 2.
Device group separation behaviour
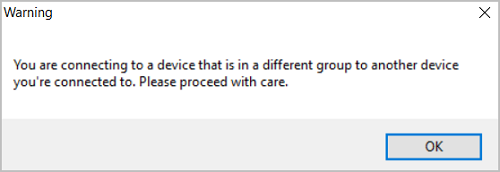
Device group separation behaviour can be changed from the default Block setting (meaning devices from multiple groups can't be accessed at the same time) to a Warn setting. Selecting Warn means that a warning message appears when a user tries to connect to two devices from different groups, but the user can still continue to access both devices.
To configure the separation:
-
Click on the
 icon.
icon. -
Select the Warn value from the drop-down box.
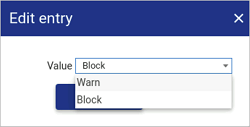
-
Click
SAVE.Now when a user opens up two connections to a device in different device separation groups, they won't be blocked but will be presented with a warning:
Network settings tab
The Network settings tab allows you to configure the following settings on Osirium PAM:
- NTP Status
- DNS servers
- DNS search suffix
- NTP server
- Syslog server
- Use CEF formatted syslog messages
- Logstash server
- SMTP configuration
- Send emails in plain text format
- SNMP configuration
- Combine password and token code for RADIUS-only users
- Require token at time of login for RADIUS-linked users
- RADIUS configuration
- Remote backup and archive server
- SMB share backup configuration
- RDP keepalive enabled
NTP Status
When an NTP server has been configured, the NTP Status button displays details of the PAM Server and NTP server status. These details can assist when troubleshooting NTP server synchronisation issues.
-
Click on the
NTP STATUSbutton.
-
The following details are displayed:
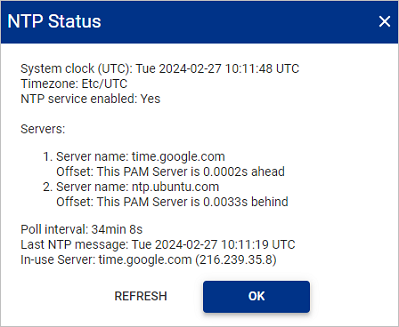
Field name Description System clock (UTC) The current UTC date/time of the PAM Server. Timezone The timezone of the PAM Server. NTP service enabled Displays if the NTP service is enabled or disabled. Server name The NTP server configured on the PAM Server. NOTE If multiple NTP servers have been configured, each NTP server will be listed.
Offset The time offset in seconds of the NTP server compared to the PAM Server. NOTE A negative value indicates the NTP server is behind the PAM Server.
Poll interval The frequency of when the PAM Server contacts the NTP server. Last NTP message The date/time that the PAM Server last received a message from the NTP server. In-use Server The NTP server currently being used by the PAM Server. The following issues were detected Details of any reported issues. -
To refresh the NTP status details click
REFRESH. -
Click
OK.
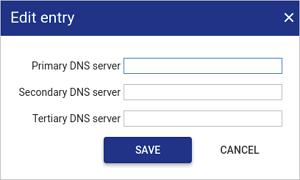
DNS servers
To set DNS servers:
-
Click on the
 icon.
icon.
-
Set the primary, secondary and tertiary servers as required.
-
Click
SAVE.
DNS search suffix
Adding DNS search suffix entries will help resolve IP addresses when adding new devices.
To add a DNS search suffix:
-
Click on the
 icon next to DNS Suffixes. DNS search suffix 1 will be added.
icon next to DNS Suffixes. DNS search suffix 1 will be added. -
Fill in the suffix:
-
Click
SAVE.
NTP server
To set an NTP server:
-
Click on the
 icon next to NTP server. NTP server 1 will be added.
icon next to NTP server. NTP server 1 will be added. -
Click the
 icon for NTP server 1.
icon for NTP server 1. -
Enter the IP Address or pool of the NTP servers.
-
Click
SAVE.Tip
You can add multiple NTP servers by clicking the
 icon several times.
icon several times.
Syslog server
Osirium PAM can send copies of its syslog messages to as many external syslog servers as you wish.
To add an external Syslog server:
-
Click on the
 next to Syslog server. Syslog server 1 will be added.
next to Syslog server. Syslog server 1 will be added.
-
Click the
 icon for Syslog server 1.
icon for Syslog server 1. -
Enter the IP Address of the Syslog server Osirium PAM will be communicating with.
-
Click
SAVE.
Use CEF formatted syslog messages
Enabling this setting allows Osirium PAM to use the CEF formatting standard when displaying syslog messages.
To enable:
-
Click on the
 icon.
icon. -
Check the Enabled box.
-
Click
SAVE.
Logstash server
Enter your logstash server details to allow Osirium PAM to push events to your logstash server.
To add a logstash server:
-
Click on the
 icon.
icon.
-
Fill in the details.
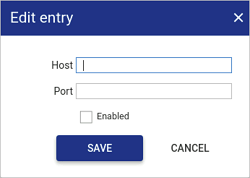
Field name Description Host: Enter the host name or IP address of the logstash server. Port Enter the port number assigned to the logstash server.  Enabled
EnabledEnabling will allow Osirium PAM to connect to the logstash server. -
Click
SAVE.
SMTP configuration
Configure the SMTP to allow emails to be sent from the PAM Server. SMTP is required if you want to setup Email subscriptions, see Managing Email Subscriptions.
Note
The SMTP server must support TLS (Transport Layer Security) to ensure passwords are not sent in plain text.
To configure SMTP:
-
Click on the
 icon.
icon.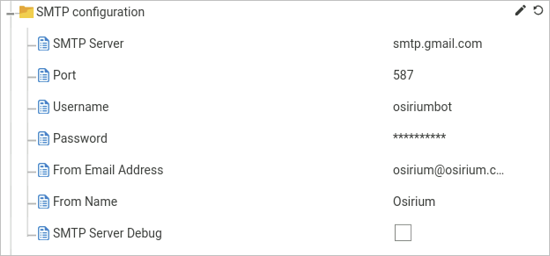
-
Fill in the details.
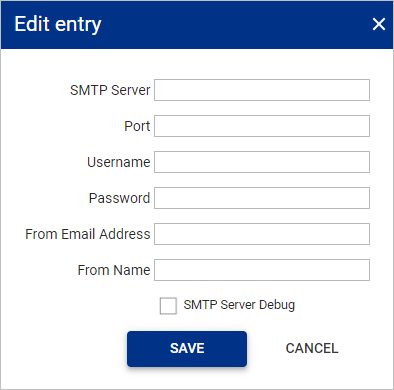
Field name Description SMTP Server IP address of the SMTP server. Port Enter the port number assigned to the SMTP server. Username Enter the username that will be used to authenticate onto the SMTP server. Password Enter the password that will be used to authenticate onto the SMTP server. From Email Address Used to set the Reply-To and Sender headers user@domain of the outbound email. From name Used to set a text description in the Reply-To and Sender headers of the outbound email. SMTP Server Debug This allows email server transaction messages to be directed to the mail.log file -
Click
SAVE. All members of the Owner and Admin roles will receive an email to confirm that email has been successfully configured.
Send emails in plain text format
By default all emails sent from Osirium PAM are in HTML format. Osirium PAM can be configured to send all emails in plain text.
To configure all emails to be sent in plain text format:
-
Click on the
 icon.
icon.
-
Check the Enabled box.

-
Click
SAVE.
SNMP configuration
Configure SNMP to allow Osirium PAM to be monitored on your network.
To configure SNMP:
-
Click on the
 icon.
icon.
-
Fill in the details.
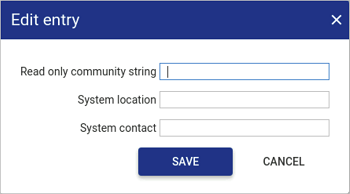
Field name Description Read only community string Enter a valid read-only community string to allow SNMP requests to be sent. System location Enter the location of Osirium PAM. System contact Enter a valid contact name for Osirium PAM. -
Click
SAVE.
Combine password and token code for RADIUS-only users
Enabling this setting combines the password and token code. This only applies to RADIUS only users.
When users login, they will be presented with: a Password field; and a Token code field. If the user is only configured for RADIUS authentication (i.e. they are not using Local then RADIUS or Active Directory then RADIUS, see Manage users, then the way in which the Password and Token code fields are presented to the RADIUS server can be controlled here.
By default this setting is ENABLED (checkbox ticked) which means the Password and Token code fields will be joined together and sent as one RADIUS Access-Request. For example: With a Password of p4ssw0rd and a Token code of 12345, the RADIUS Access-Request will contain the combined User-Password of p4ssw0rd12345.
This setting will also be useful if:
-
Your RADIUS server is expecting the two parts concatenated e.g. an RSA RADIUS server expecting the user's password and token code in the same Access-Request.
-
Users only enter a secret. Not all RADIUS configurations will require a user to authenticate using both a password and a token code. Users may also not be familiar with the authentication mechanism and therefore they will either think of their one secret as a password or a dynamic token. By enabling this setting, the user can enter their one secret into either the Password or Token code field and the RADIUS server will still be sent the correct Access-Request.
Not combining the fields will be necessary if it is known that the RADIUS server will issue a follow-up Access-Challenge.
DISABLING (checkbox unticked) this setting will mean that only the Password will be sent in the initial RADIUS Access-Request. If the RADIUS server replies with Access-Challenge, then the Token code in the subsequent RADIUS Access-Request.
Note
Microsoft Azure Multi-factor authentication (MFA)
It is possible to configure RADIUS access to Azure MFA by setting up a Network Policy Server. With Azure MFA, users can choose whether they set up push-based or token-based MFA.
For token-based MFA, a Network Policy Server will issue a follow-up Access-Challenge, we therefore recommend DISABLING (checkbox unticked) the Combine password and token for RADIUS-only users setting to provide compatibility for both push-based and token-based users.
To enable:
-
Click on the
 icon.
icon. -
Check the Enabled box.

-
Click
SAVE.
Require token at time of login for RADIUS-linked users
By default the token code field is displayed on the user login window for all users with RADIUS linked authentication types.
To configure the token code field to not be displayed for RADIUS linked authentication types:
-
Click on the
 icon.
icon.
-
Un-check the Enabled box.
-
Click
SAVE.
RADIUS configuration
For Osirium PAM users to be authenticated through RADIUS, configure the RADIUS settings.
To configure Radius:
-
Click on the
 next to RADIUS configuration. RADIUS configuration 1 will be added.
next to RADIUS configuration. RADIUS configuration 1 will be added.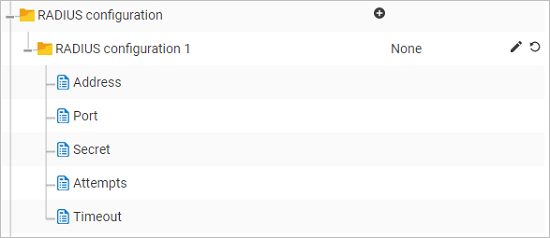
-
Click the
 icon for RADIUS configuration 1.
Fill in the following details:
icon for RADIUS configuration 1.
Fill in the following details: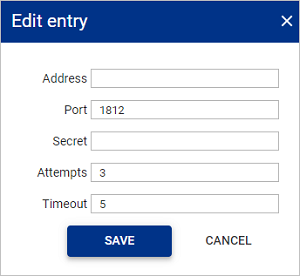
Field name Description Address Enter the IP Address of the RADIUS server. Port Enter the port number assigned to the RADIUS server service. Secret Enter the RADIUS Secret that will be used to authenticate onto the RADIUS server. Attempts Enter the number of times you want a user to attempt the connection before it fails. Timeout Enter the minutes allowed before the connection is timed out. -
Click
SAVE.
Remote backup and archive server
If the remote backup and archive server is configured, Osirium PAM will automatically push Osirium PAM backup files to the specified location at the end of the backup task.
To setup remote backup:
-
Click on the
 icon.
icon.
-
Within the Edit entry window, select the required option:
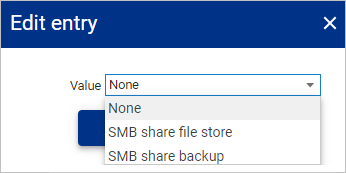
Field name Description None Setting not configured. SMB share file store Selecting this option will push Osirium PAM backup files to the SMB share location specified within the System settings > SMB share configuration setting. NOTE
- Ensure the System settings > File store setting is set to SMB share.
- Ensure the System settings > SMB share configuration settings have been configured.
- A folder named Backup will be created on the SMB share.
- The Osirium PAM backup files will be pushed to the Backup folder and the specified SMB share configuration folder.SMB share backup Selecting this option will push Osirium PAM backup files to a folder named Backup on the SMB share backup configuration location. NOTE
- Ensure the Network settings > SMB share backup configuration settings have been configured.
- If the System settings > SMB share configuration settings have been configured, the Osirium PAM backup files will be pushed to the Backup folder in addition to being pushed to the SMB share configuration folder. -
Click
SAVE.
SMB share backup configuration
Configuring the SMB share backup configuration will allow your PAM Server to push Osirium PAM backups directly onto an SMB share location.
| Field name | Description |
|---|---|
| UNC path | The UNC path by which PAM can connect to the SMB share. For example \\server-name\shared-resource-pathname |
| Username | The username of the SMB share location. For example \domain\username |
| Password | The password of the SMB share location. |
Note
After configuring the SMB share, navigate to the System queue and confirm the Device sync parameters setup task was successful.
RDP keepalive enabled
Enabling this setting prevents the screensaver from being activated.
To enable:
-
Click on the
 icon.
icon. -
Check the Enabled box.

-
Click
SAVE.