Vaults
Overview
PPA tasks require connection details & secrets in order to connect to third-party systems.
These secrets must never be stored in task playbooks or configuration files.
Instead, external secret stores should be used to keep secrets safe, & refresh them if applicable.
Vaults provide a secure interface between PPA tasks & these external secret stores.
Adding a secret store as a vault allows tasks to access & use secrets from that store.
Revealing Secrets
Connecting to a secret store's API requires authentication.
When adding a vault to PPA you will need to provide some API credentials for PPA to use.
If a task requests secrets from that vault, the PPA appliance will:
- Connect to the credential store
- Access the requested secret
- Send only that secret's value back to the task
This workflow guarantees that:
- Tasks only get the values for the secrets they asked for
- The secret store's API credentials are not supplied to the task
Default Vault
The PPA appliance includes a running instance of Hashicorp Vault on the same virtual appliance.
You can configure this vault during deployment by following the instructions here.
Adding Vaults
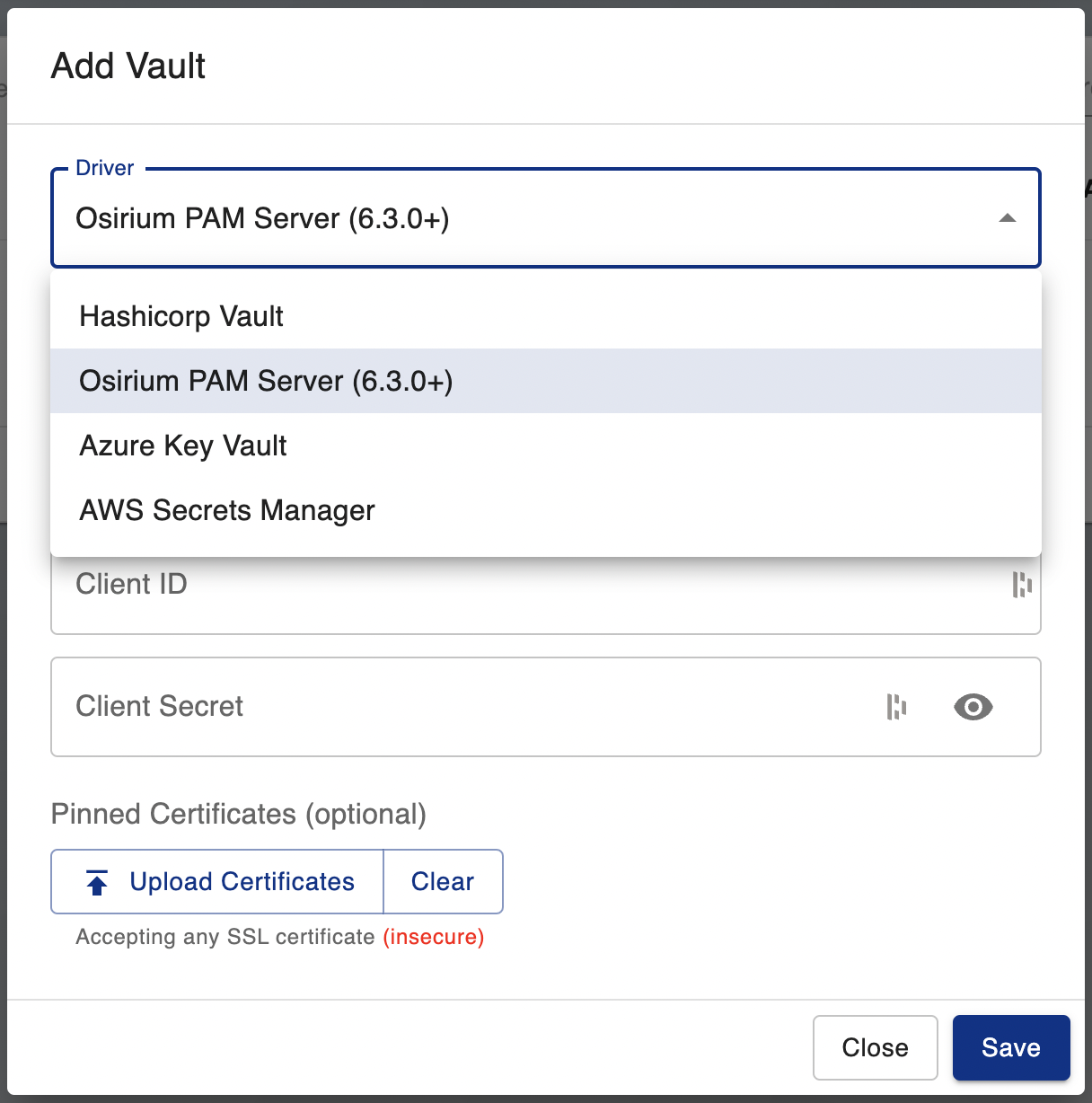
PPA currently supports the following secret stores:
- Osirium PAM
- Azure Key Vault
- AWS Secrets Manager
- Hashicorp Vault
To add a vault you will need to:
- Select the type of vault
- Provide the relevant API credentials (depending on vault type)
- Supply a certificate to use when authenticating to the vault (optional)
When the form is submitted, PPA will connect to the vault & check the credentials.
Using Vaults
Use the following plugins to use a vault from inside a task: